Product Overview
Access Manager Plus is a constructive platform to achieve secure remote access management and session governance. It allows you to establish privileged sessions to underlying systems (Windows and Linux) via a centralized console; monitor, join, record or terminate sessions effectively.
It allows you to define roles for users and grant required privileges or access rights for those roles. It also allows you to distribute the user information and access grants to all devices and systems that enforce access rights in the organization. Furthermore, it lets you monitor and assess the privileged users' activities to detect anomalies.
On the whole, Access Manager Plus provides real-time monitoring and control of access and sessions of all privileged users, to counteract malicious activities.
Manage Engine Access Manager Plus is a web-based privileged session management software for regulating access to remote systems through secure channels from a unified console. With comprehensive auditing capabilities, it offers total visibility into all privileged access use and lets enterprises manage privileged user sessions in real time, shutting the door on privilege misuse.
Specifications
1. Central control and management
Centralization or centralized management in IT terms is when critical decisions and policies are enforced by a few top leaders within the organization from a single point of control.
The need for centralized, secure remote access
Today’s complex and heterogeneous corporate environments require security heads to manage and govern access to a growing inventory of remote servers, computers, and other IT assets. However, relying on multiple legacy remote access tools is inefficient and presents huge security risks. This calls for a simple, secure remote access solution that streamlines privileged access to critical systems, irrespective of their disparate network topologies.
A single point of control
-Access Manager Plus facilitates centralized administration of distributed remote IT assets through a web-based solution.
-Privileged users can update, troubleshoot, and manage remote servers centrally. These activities are recorded and stored as video files and audit logs within the application.
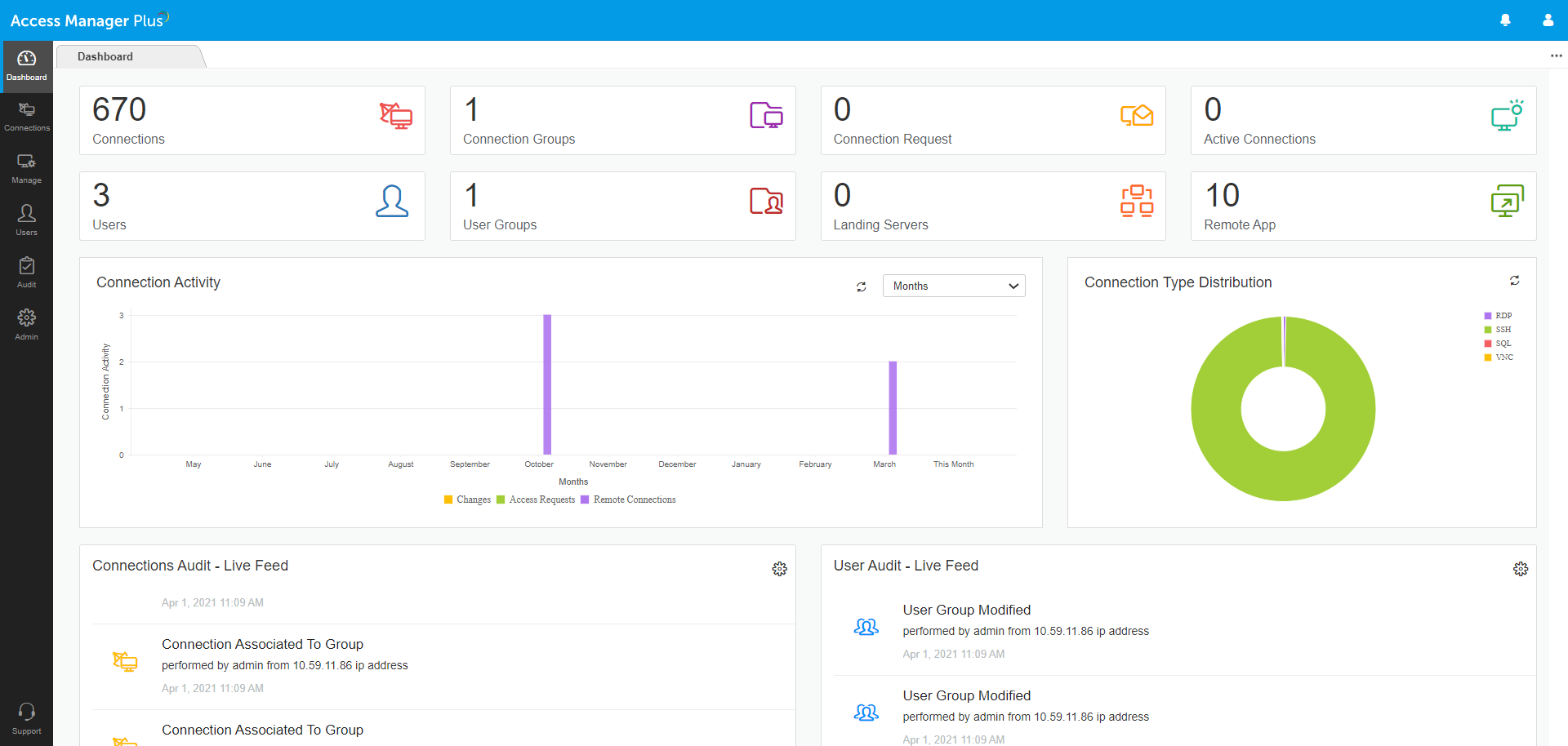
-The dashboard displays at-a-glance information on privileged access activities, which helps with quick, efficient administration.
-Administrators can view live updates on privileged remote access and the number of connections, landing servers, access requests, etc. right from the dashboard.
-Ensure improved quality of work and better accountability through standardized policies and efficient supervision.
Discover, add, and organize remote connections
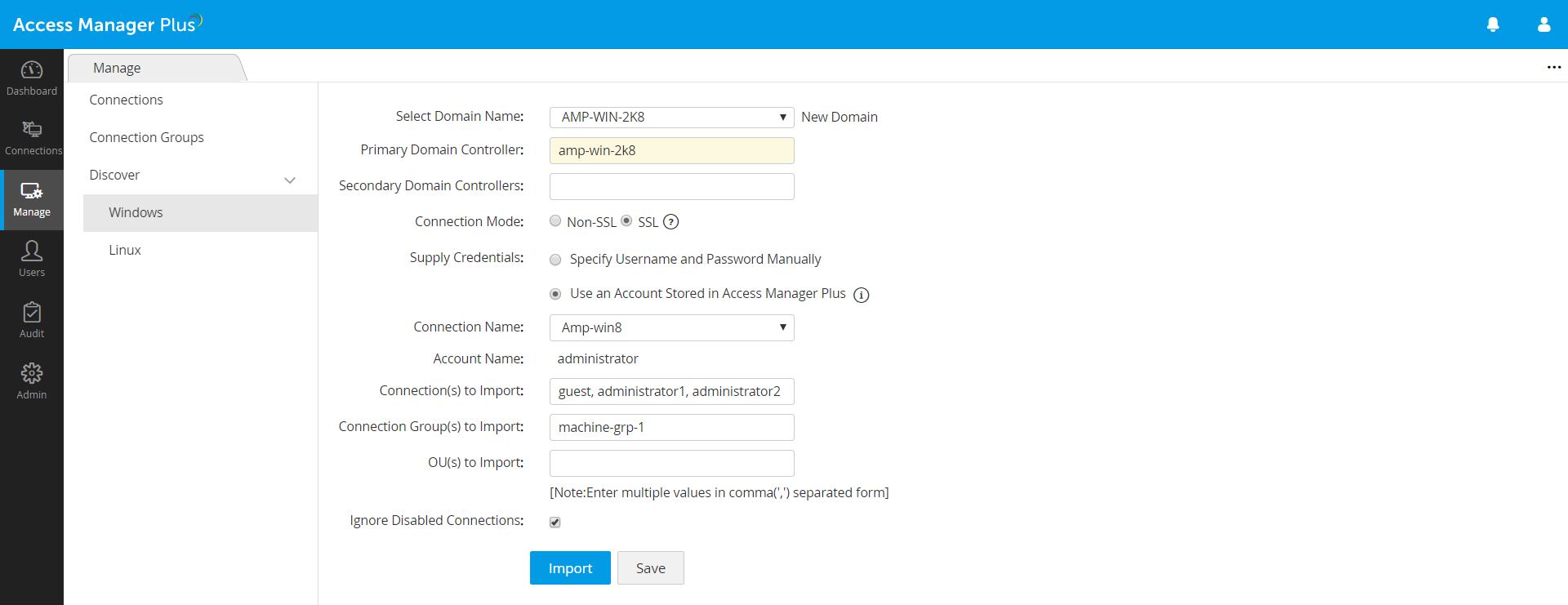
-Scan networks and automatically discover flavors of Windows and Linux systems, along with their associated privileged accounts, and add them as remote connections in Access Manager Plus.
-You can also manually add connections or import them from a CSV file.
-Declutter your database with Access Manager Plus’ grouping options. Organize your connections into groups, and configure the required settings for all the connections associated with a particular group at once.
Establish central control on access pathways
-Do away with multiple remote access tools, and enable VPN-less connections to remote servers and systems through secure RDP, SSH, SQL, and VNC pathways.
-Provide users with role-based access to critical systems based on preset user privileges and access controls.
-Allow or restrict specific client system access to Access Manager Plus by whitelisting or blacklisting IP addresses.
2. Authentication methods
The need for two-factor authentication for remote access
Authenticating a user before providing them with access to critical systems is crucial for enterprises to defend against cyberattacks. The username-password combination has long been the traditional method of user authentication, although passwords are rarely unique to the user. However, compromised and weak passwords can be exploited by anyone to access a corporate network, putting organizations at risk. To counter such risks, enterprises need to implement a multi-layered, defense-in-depth approach to user authentication.
Given the nature and scope of remote access activities and the entitlements available to a privileged user, enterprises must include two-factor authentication (2FA) in their remote access strategy to improve security and accountability. Currently, many compliance standards like PCI-DSS, HIPAA, and NERC-CIP specifically require that remote access tools implement 2FA for granting remote access to critical systems. Failure to meet these regulatory standards by any organization could wreck its reputation and incur significant fines.
Access Manager Plus integrates with various tools available on the market for primary and secondary factors of authentication, helping organizations adopt a strong, well-defined 2FA architecture to meet security requirements.
Primary factor of authentication
Active Directory (AD)/Azure AD authentication: Leverage Microsoft’s AD authentication and single sign-on capabilities for Windows-based systems to allow users to log in to Access Manager Plus with their AD or Azure AD credentials. Moreover, users already logged in to their Windows applications with their directory credentials can log in to Access Manager Plus without supplying credentials.
Lightweight Directory Access Protocol (LDAP) authentication: When Access Manager Plus is installed in a Linux/Unix system, administrators can use LDAP to authenticate users from any LDAP-compliant directory. LDAP is operating system (OS)-agnostic; it can talk to any directory service irrespective of the OS, including Windows AD.
RADIUS-based authentication: Administrators using RADIUS as the directory service inside their organization can use it as the primary authentication method to log users into Access Manager Plus. They can import user information from the RADIUS server, sync role information, and also perform user authentication in real time.
Single sign-on (SSO): An SSO system grants access to multiple systems with a single set of login credentials. Access Manager Plus supports SSO through SAML-based authentication for Okta, Azure AD, and Active Directory Federation Services (ADFS), and through NTLM-based authentication for on-prem AD. Upon activation, users already logged in to the system with their Okta, Azure AD, ADFS, or AD credentials will be automatically authenticated into Access Manager Plus using the respective protocols.
Smart card PKI/certificate authentication: Access Manager Plus' web interface supports smart card technology with SSL client certificate authentication. Administrators with a smart card authentication system in their environment can configure Access Manager Plus to authenticate a user with their smart card, mandating them to provide their personal identification number (PIN) and X.509 certificate to login.
Local authentication: Besides the above options, an authentication database is built into Access Manager Plus, making it a local authentication server. Typically, you can create local user accounts for temporary users who do not have accounts on your enterprise servers, and for administrators and privileged users for break glass purposes. The built-in password generator can be used to generate passwords according to the policy enforced by the system administrator.
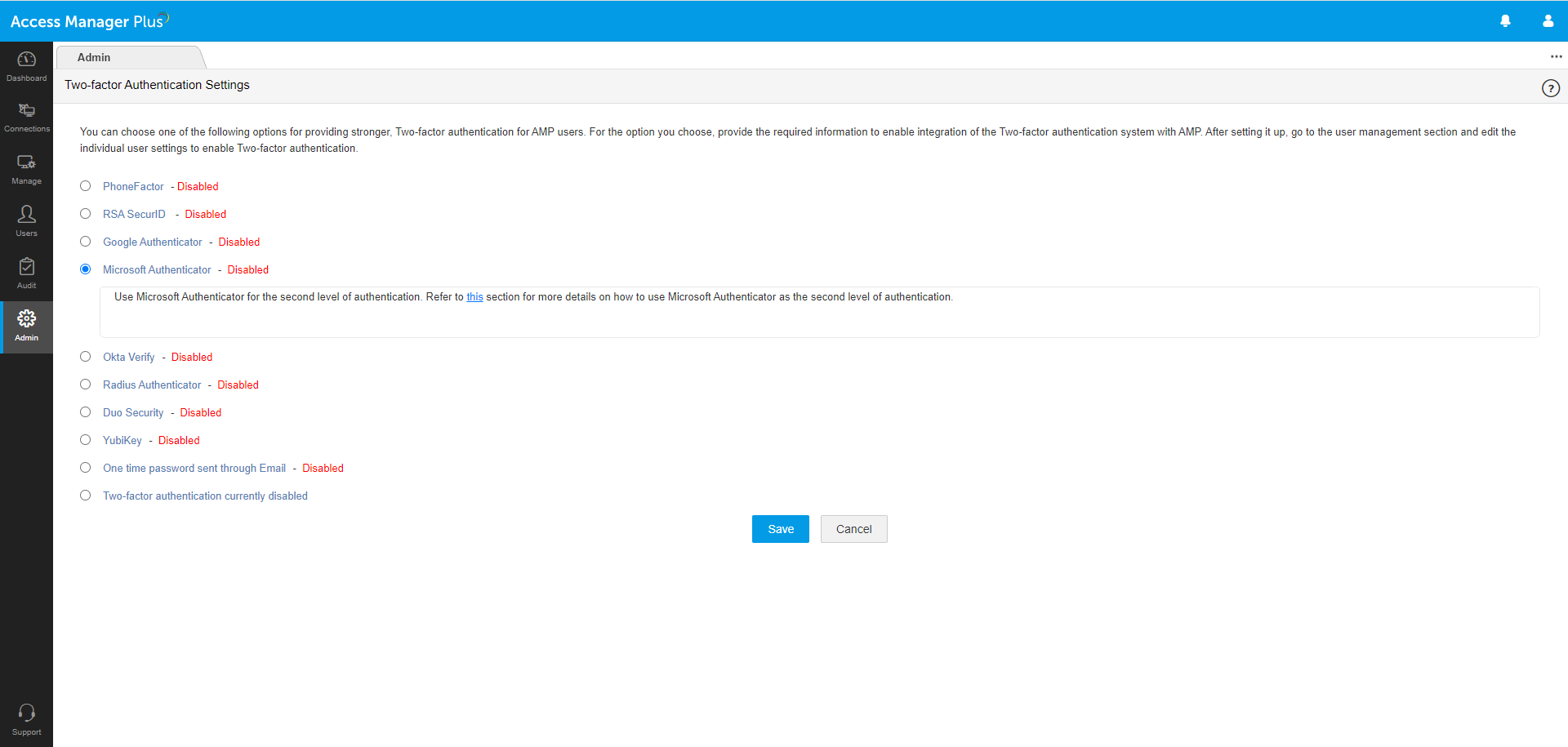
Secondary factor of authentication
Unique password through email: Send a unique one-time password (OTP) to users via email as the secondary factor of authentication. This OTP expires after a stipulated time period.
Windows Azure Multi-Factor Authentication: Formerly called PhoneFactor, this leading global provider of phone-based 2FA enables simple and effective security by placing a confirmation call to a user’s phone during the login process.
RSA SecurID Access: This application generates a software token, which usually changes every 60 seconds. After providing the first factor of authentication, a user needs to enter both a PIN and the corresponding RSA SecurID token code as the secondary factor of authentication.
Time-based one time password (TOTP): TOTP is part of the open authentication (OAuth) security architecture, and is an automatically generated numeric string of characters that authenticates a user and expires after a certain time period. Access Manager Plus supports any third party TOTP-based authenticator, like Google Authenticator, Microsoft Authenticator, and Okta Verify.
RADIUS-based 2FA: Access Manager Plus integrates with any RADIUS-compliant system, like Vasco Digipass, AuthAnvil, or PingIdentity, to accomplish 2FA. Upon successful primary authentication, a user must provide the RADIUS code similar to a TOTP as the secondary factor of authentication.
Security: Duo Security is a vendor of cloud-based 2FA services that lets users log in to Access Manager Plus through a mobile app, a text message, or a phone call.
YubiKey: YubiKey is a hardware key that supports OTPs, public key encryption, and authentication. After the primary authentication, a user needs to insert their YubiKey into the USB port of their laptop or computer to generate an OTP and provide it as the secondary factor for successful authentication.
3. User management
The need for a central console for user management
Enterprises today depend on a range of user directories to manage users. For example, Active Directory (AD) is the main user directory in a Windows-dominated network, and Lightweight Directory Access Protocol (LDAP) is mostly preferred for Linux systems. Apart from the primary directories, there might also be an internal directory or other types of user directories in place to manage diverse user accounts. Employing multiple directories not only makes user administration difficult but also increases management overhead.
Access Manager Plus’ built-in user management module
-Access Manager Plus enables administrators to seamlessly integrate users and facilitate their authentication, authorization, and access—all from a single point of control. Access Manager Plus’ user management module:
-Helps administrators limit access to critical enterprise systems to authorized users.
-Provides insights into the assignment and distribution of user-based licenses so administrators can use licenses more effectively.
-Enables administrators to log users out of the application automatically after a specified period of inactivity, modify their configured settings, and lock or delete them permanently.
-Facilitates the transfer of resource ownership when an employee leaves the organization or moves to another team within the organization.
-Helps monitor user access and address violations of defined policies.
Onboard, authenticate, and authorize users
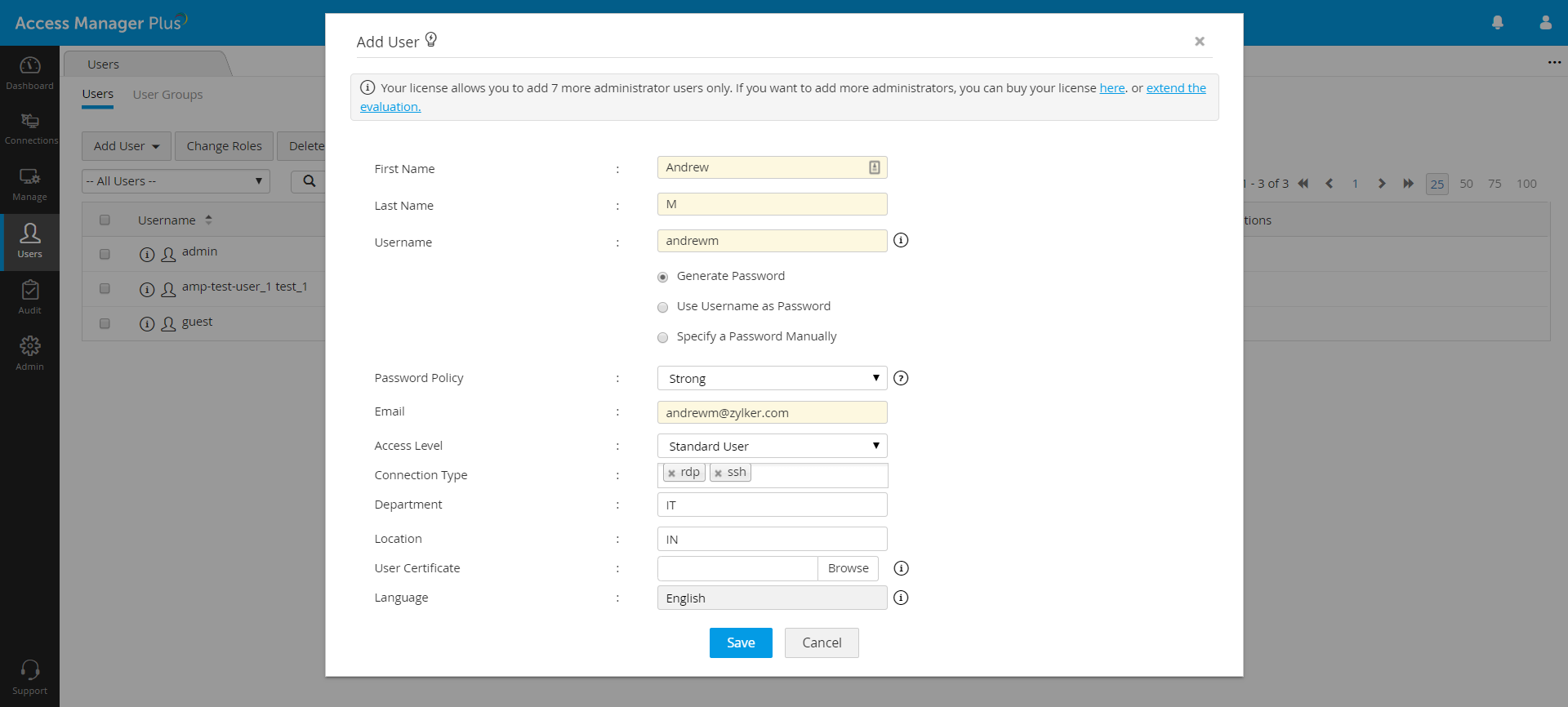
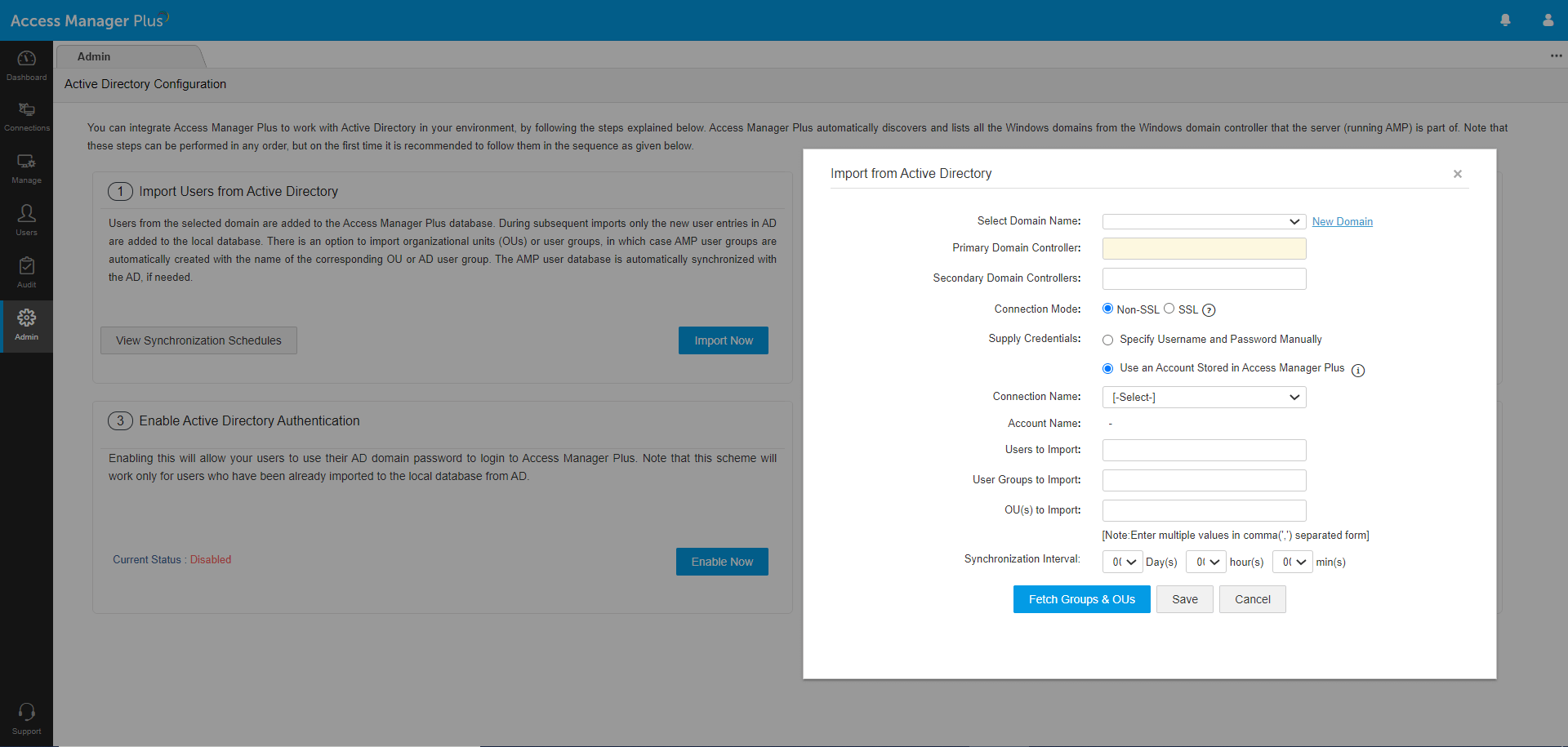
Administrators can either add users to Access Manager Plus manually or import them from CSVs, TXT files, or user directories.
Leveraging the directory setup saves a substantial amount of time in the onboarding process by enabling quick user import and authentication. The user database in Access Manager Plus constantly synchronizes with the directory and is automatically updated whenever users are added to or removed from it.
Access Manager Plus helps organizations adopt a well-defined two-factor authentication architecture by integrating with various tools available in the market for primary and secondary factors of authentication.
After defining the authentication mechanism for users, administrators can authorize them by defining their access scopes or privileges, thereby granting or denying them permission to access a resource.
Replicate user groups from directories or create custom user groups
Integrating Access Manager Plus with AD, LDAP, or Azure AD helps with importing user groups directly from the directory with the same hierarchical structure. Administrators can also combine users into custom user groups based on the resources they can access; their role, permissions, team, or department; or other functionalities. With user groups, administrators can quickly set preferences and assign functions for users in bulk.
Assign default or custom roles for users
With the rising number of IT assets and applications available to users at their fingertips, it’s increasingly important for administrators to define role-based controls for users and provision access to various IT resources based on need. Apart from the two predefined user roles, i.e., Administrator and Standard User, Access Manager Plus enables administrators to create custom roles from scratch, specifying the desired permissions for each role, and then assign them to users or user groups.
4. Access control workflow
The need for granular controls for remote access
Many recent cyberattacks substantiate that granting internal IT staff and third-party contractors uncontrolled access to critical systems can cause serious security problems and increase risk.
The more users with access to privileged credentials, the higher the risk that attackers could get unrestricted access to the IT network. Organizations that provide unfettered access to all users often lack visibility into the operations performed with such access. Limiting and controlling privileged access must be an essential part of IT security workflows to minimize the risk of uncontrolled privileged access.
An access control workflow helps administrators provide authorized, controlled access to remote resources. In-depth audit trails that capture all the details of remote access, including who requested what access, why, and who approved the request, also help in fortifying the access control workflow.
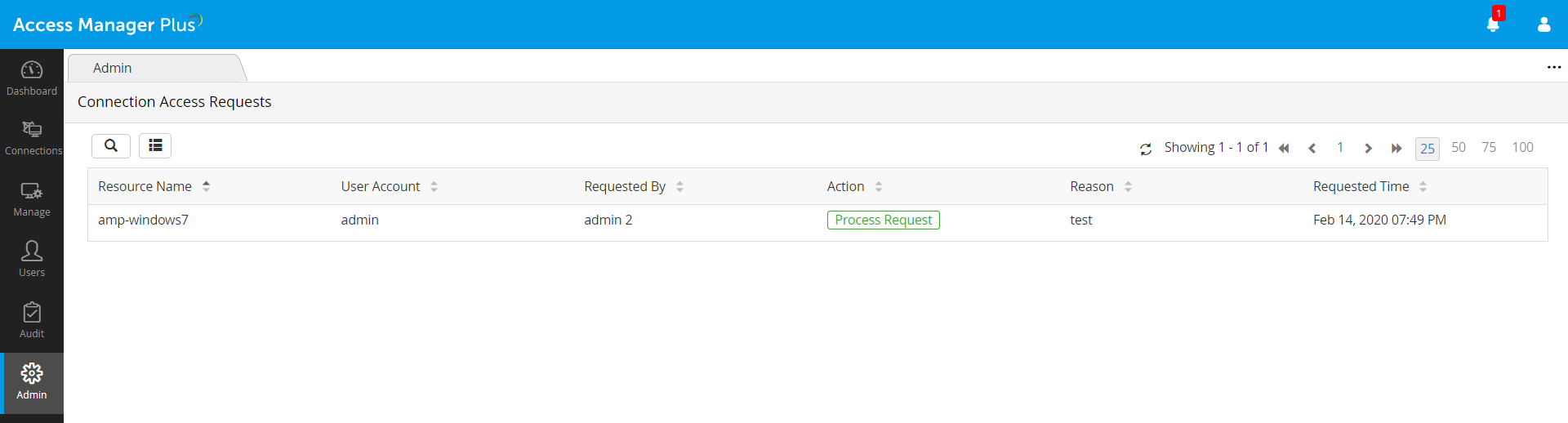
Request-approve-release workflow in Access Manager Plus
Access Manager Plus allows users to restrict access to the connections they’ve added. Unless the request to access a particular connection is approved by the owner of the connection, others will not be able to launch a remote session to that connection or view its password.
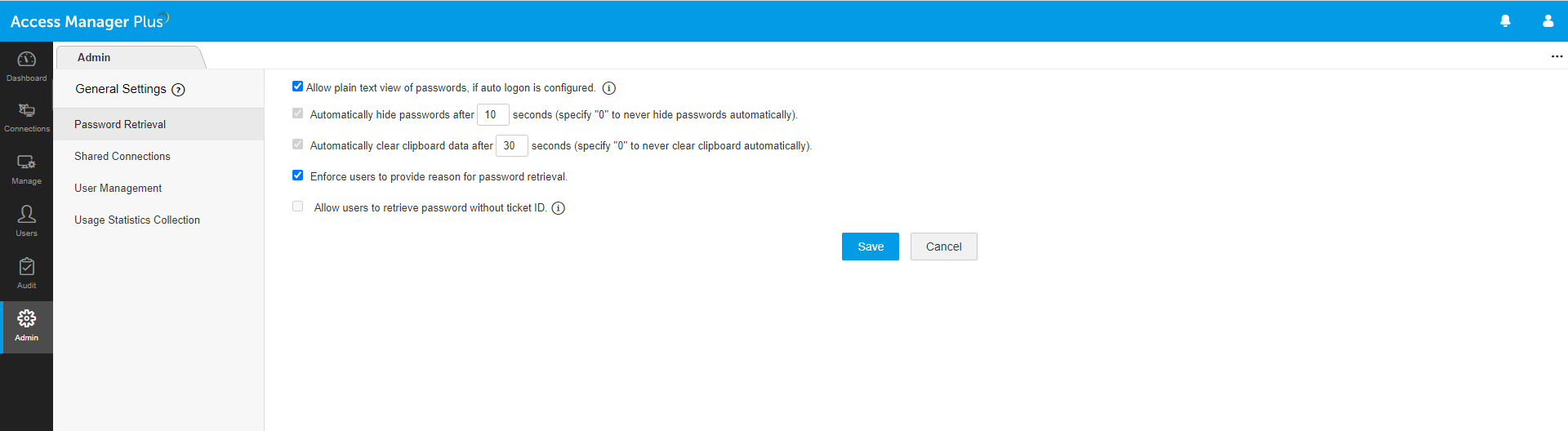
Require users to provide a reason before password retrieval
You can mandate users requiring access to a remote connection to raise a request and provide a credible reason. This allows the connection owner to scrutinize access requests before approval and reject inappropriate requests.
Time-bound privileged access
Upon authorizing access requests, provision users with temporary access to the remote connection for a specified time frame. By default, Access Manager Plus automatically revokes a user’s access after 30 minutes from the time they check out a password. Through session shadowing, administrators can detect a suspicious session in real time and forcefully check in the corresponding password before the stipulated time expires.
Restrict simultaneous password checkouts
Access Manager Plus enables administrators to prevent multiple users from simultaneously accessing a particular connection. Only one user can check out the password for a remote connection at a time. If another user requests access to a password that’s in use and their request is approved, they’ll be allowed access only after the current user checks in the password.
Control password exposure
For further security, administrators can prevent the exposure of passwords in plaintext while providing access to the desired connections. In such cases, users will be able to launch a remote connection through Access Manager Plus’ auto-logon feature. If plaintext view of passwords is enabled, administrators can choose to hide the passwords after a specified time.
5. Ticketing system integration
What is a ticketing system?
A ticketing system is a program that helps enterprises centrally manage their customer or staff queries in the form of service tickets. In privileged access control terms, a ticketing system is used by IT teams to address remote access needs by assigning a service ticket to the access request.
Granting internal employees and third-party vendors unlimited access to critical systems increases the risks of attackers getting unrestricted access to an IT network. Limiting privileged access with ticketing systems is an essential part of minimizing the risks of uncontrolled privileged access in your IT security workflows.
The benefits of using a ticketing system for remote access
Access controls along with a ticketing system enable IT teams to:
-Verify access to privileged accounts and ensure users are authorized to access an endpoint.
-Ask why users need access to specific endpoints.
-Organize service events into a searchable database.
-Get a detailed history of what actions were taken, when, and by whom.
-Create a strong traceable audit trail on remote access activities that can be reviewed by auditors and forensic investigators.
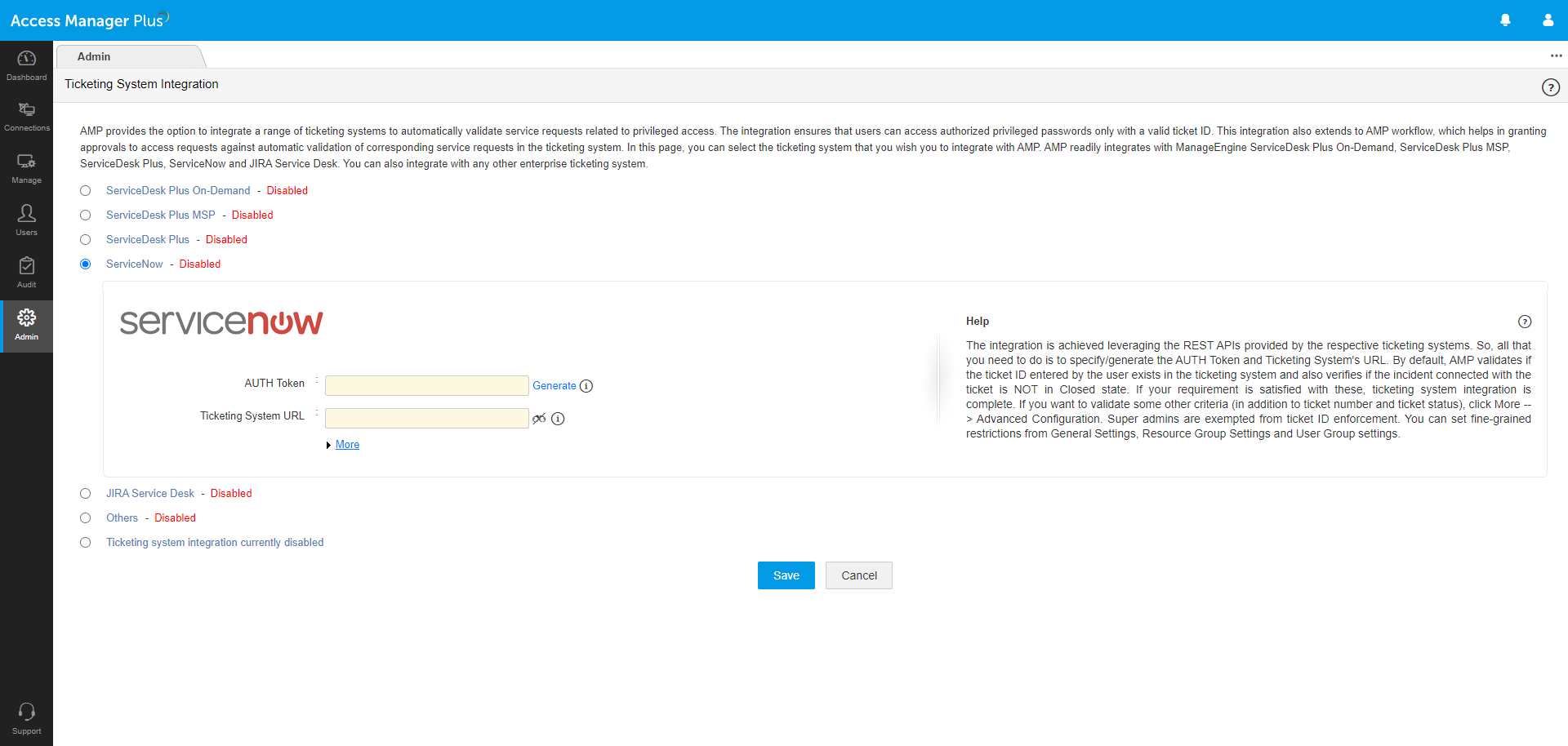
Integrating ticketing systems into Access Manager Plus
Access Manager Plus integrates with leading ticketing systems to automatically validate service requests related to privileged access. This integration ensures only users with a valid ticket ID can access the resources stored in Access Manager Plus, which is especially helpful with managing third-party and insider access to the most critical endpoints.
Improved accountability
Once integrated with a ticketing system, authorized users simply have to select the resource they need access to, specify the reason for access, and provide the corresponding ticket attribute. Before granting access, Access Manager Plus will:
-Validate that the ticket ID entered by the user exists in the ticketing system and is still open.
-Ensure that the user who opened the ticket is authorized for privileged access to the relevant systems and applications.
Apart from ticket ID and status, Access Manager Plus’ advanced settings let you define custom criteria and validate them with the ticketing system before granting access to passwords. Access Manager Plus offers total flexibility to check for any parameter in the ticketing system, including any additional fields you add.
Supported ticketing systems
Out of the box, Access Manager Plus integrates with:
-ServiceDesk Plus On-Demand
-ServiceDesk Plus MSP
-ServiceDesk Plus
-ServiceNow
-JIRA
6. Data center remote access
What is a jump server?
A jump server is an intermediary landing server, a host device, or an SSH gateway that enables users to connect to and manage remote systems in different security zones, and facilitates controlled access between them.
The need to secure remote access through jump servers
To use a jump host, users first launch an RDP connection to the jump host, identify the target host they want to connect to, make the connection between the jump host and the target, and then finally access the target machine. This entire process often requires providing the IP address or hostname of the target machine you want to access and manual authentication at every jump server setup, introducing loopholes from a security perspective.
Jump servers enable direct access to critical remote systems in separate security zones, so credentials to connect to remote systems are key targets of cyberattacks. In addition, a malicious actor with access to a jump server can masquerade as an authorized user and control the assets that are managed through that jump server. Therefore, it’s important to protect the devices in your network from external infiltration and from spreading malware to other machines on the network.
Automate quicker connections to remote data centers
Access Manager Plus streamlines the entire process of data center access management by enabling direct connections to remote systems in a data center while adhering to the security protocols, helping you improve operational efficiency and productivity. Administrators can consolidate all remote device credentials centrally and map them to the respective jump servers. This facilitates smooth, one-click access to remote resources while the intermediary jump server authentication is automatically executed in the background.
Configure jump servers to launch a direct connection to data center resources
Access Manager Plus lets you configure any number of jump servers to connect to a remote Linux system (SSH connection) and a single jump server to connect to a remote Windows system (RDP connection). Once configured, you can associate the jump servers with the remote resources managed in Access Manager Plus, and define the path to launch a direct connection with the resource. You can associate as many remote systems as needed with a single jump server; different remote systems have different connecting paths with different intermediary hop servers.
Once the configuration is done, you can launch a direct, one-click connection to the remote resources without worrying about the intermediate hops. Access Manager Plus finds the connection path automatically, then establishes connection with the landing servers and the remote resources automatically.
7. One click remote sessions
What is secure remote access?
Secure remote access refers to an IT security strategy that allows authorized, controlled access to an enterprise network, mission-critical systems, or any confidential data. It enables IT teams to provide varying levels of access for employees and third parties based on their roles and job duties.
The need for secure remote access
Today, it’s imperative for any organization to minimize the risks associated with remote access to critical systems. While it’s essential that these teams are provisioned with uninterrupted access to systems and processes to keep the business afloat, incorporating tight security and control around remote access operations is also important to prevent privilege abuse.
ManageEngine Access Manager Plus is a secure remote access solution built to manage administrative access to remote endpoints and other critical IT systems. The solution's straightforward web interface approach routes all remote connections through an encrypted gateway, eliminating the need for insecure virtual private networks (VPNs), agents, or any other ad hoc processes, and protecting enterprise networks from malware and cybercrime.
Establish VPN-less access to remote privileged systems
Access Manager Plus allows users to launch direct terminal sessions to remote privileged systems from its browser interface. Bundled with various gateway engines, Access Manager Plus helps users invoke and tunnel connections from web clients to target systems via emulated Remote Desktop Protocol (RDP), Virtual Network Computing (VNC), SQL, or SSH sessions without the need for VPNs, agents, plug-ins, or helper programs installed on the endpoints. Once the resource supporting the remote connection is added to Access Manager Plus, the auto logon gateway becomes enabled for all users, without needing any complicated configurations.
Achieve uncompromised security for remote access
IT teams often find themselves caught between business continuity and security, trying to strike the right balance to keep processes running. Access Manager Plus helps enterprises achieve the best of both worlds by establishing central control on remote access pathways. This way, users are provisioned with one-click access to remote privileged systems, and concurrently kept under the radar of administrators throughout. In addition, this gateway approach also eliminates the need for access credentials to critical systems to be stored in users' local hosts.
Leverage session-specific configurations for a seamless remote access experience
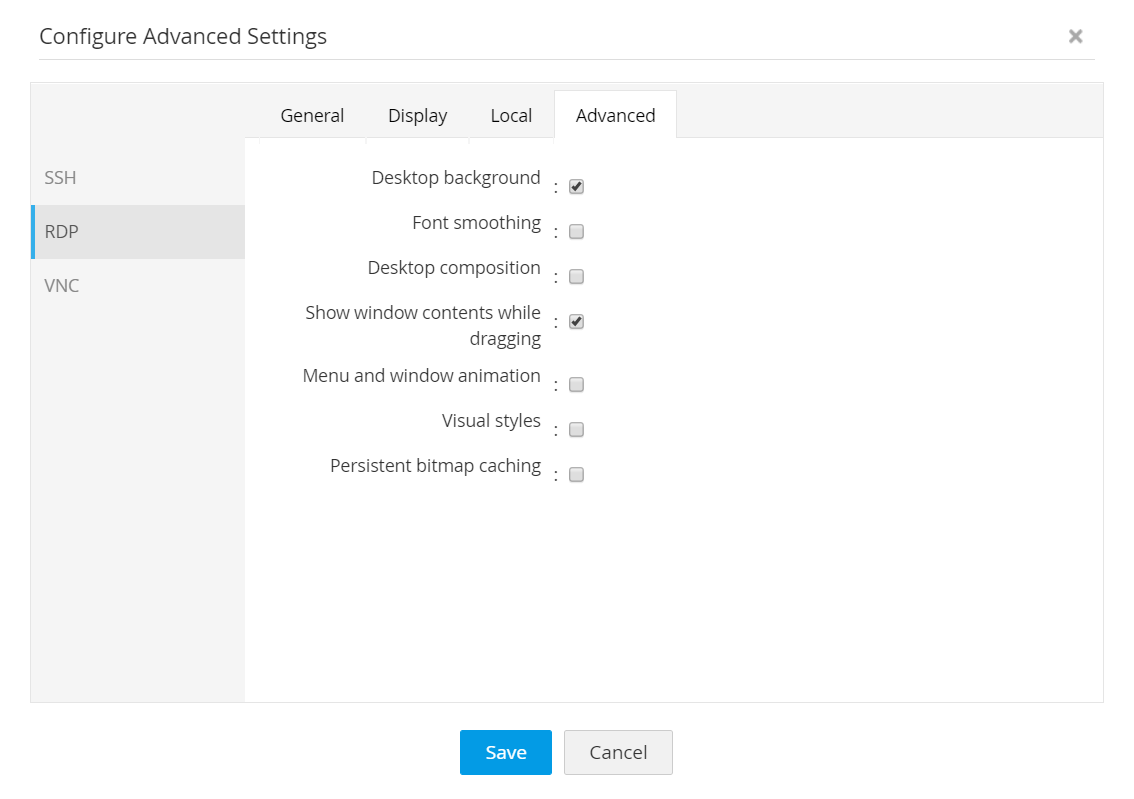
Access Manager Plus offers advanced, customizable configuration settings for RDP, SSH, and VNC connections. These settings improve the overall user experience, including the speed and performance of the remote session, while launching remote connections to the respective target systems. Some of the advanced settings include changing the SSH terminal type, configuring audio playback and printers for RDP connections, changing the encoding type of VNC connections, and more.
8. RemoteApp support for windows
RemoteApp is a remote access tool introduced by Microsoft for Server 2008 R2. It allows users to locally access specific Windows-based applications that are actually installed in a remote server. In other words, RemoteApp enables Windows applications hosted on a remote system to be be launched and managed from the local desktop like any other local application.
Configuring the RemoteApp feature to remote desktop protocol (RDP) connections increases accessibility and ease of use while connecting to remote machines. Some of the scenarios where the RemoteApp feature comes handy are:
-A user working from home wants to connect to a remote desktop server on the corporate network to run a single application, like Adobe Photoshop or Microsoft Word.
-A Mac (or any non-Windows device) user wants to use software that only runs on a Windows machine. They can run the software as a remote application on their Mac, as well as save files to their Mac or drives.
-An IT admin wants to limit a third-party user's access to a particular application, instead of an entire desktop.
The benefits of configuring the RemoteApp feature
With RemoteApp, you can integrate remote applications into a local desktop environment for a better user experience, and gives users a single platform to use both local and remote applications. They’re useful for businesses that run virtual offices, reducing the complexity of virtual desktop infrastructure (VDI) management. Configuring remote applications improves accessibility and ease of use when connecting to remote machines, and makes RDP privileged sessions more efficient. RemoteApp offers several other benefits:
-Remote applications can be launched from the Windows Start menu like any other local application, and can also be opened with Windows Search.
-Updates to the RemoteApp program, such as newly configured remote applications, automatically reflect on the user’s local desktop.
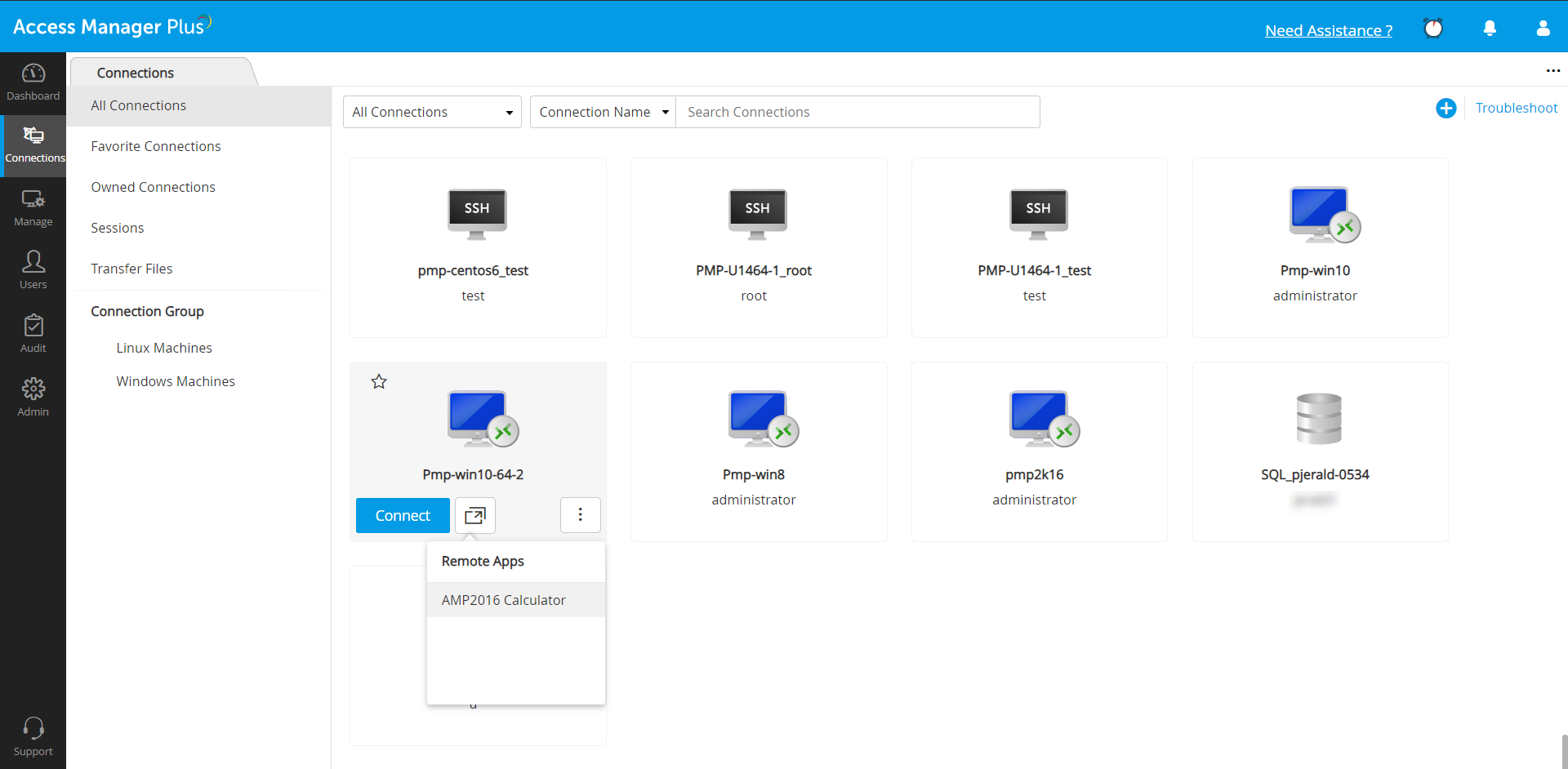
-Users can seamlessly access programs and applications on the cloud from a central location.
-Users can simultaneously manage both local and remote applications through multiple windows, without having to minimize an RDP session to access locally installed files or applications. For example, Word configured as a remote application on the remote machine, and Photoshop available on the local host, can both be launched simultaneously without affecting the user experience.
Configuring remote applications in the Windows server
To set up remote applications in ManageEngine Access Manager Plus, the RemoteApp feature must be configured in the main Domain Controller machine.
-After configuring the Windows server for RemoteApp, install the required application. If the server already has the application installed, simply configure for RemoteApp.
-Add the application to the RemoteApp programs list.
Application whitelisting in Access Manager Plus
Access Manager Plus administrators can either manually add remote applications or automatically discover them:
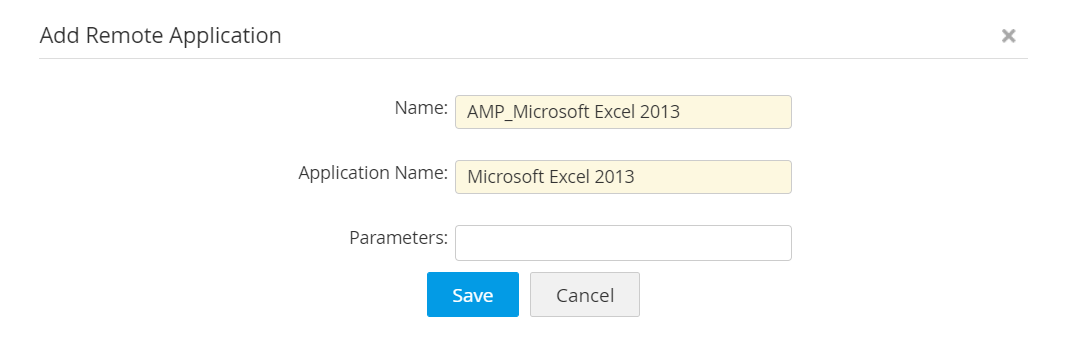
Adding remote applications manually: IT admins can simply enter the name of the remote application that has to be displayed in Access Manager Plus, and the name as it is in the remote system.
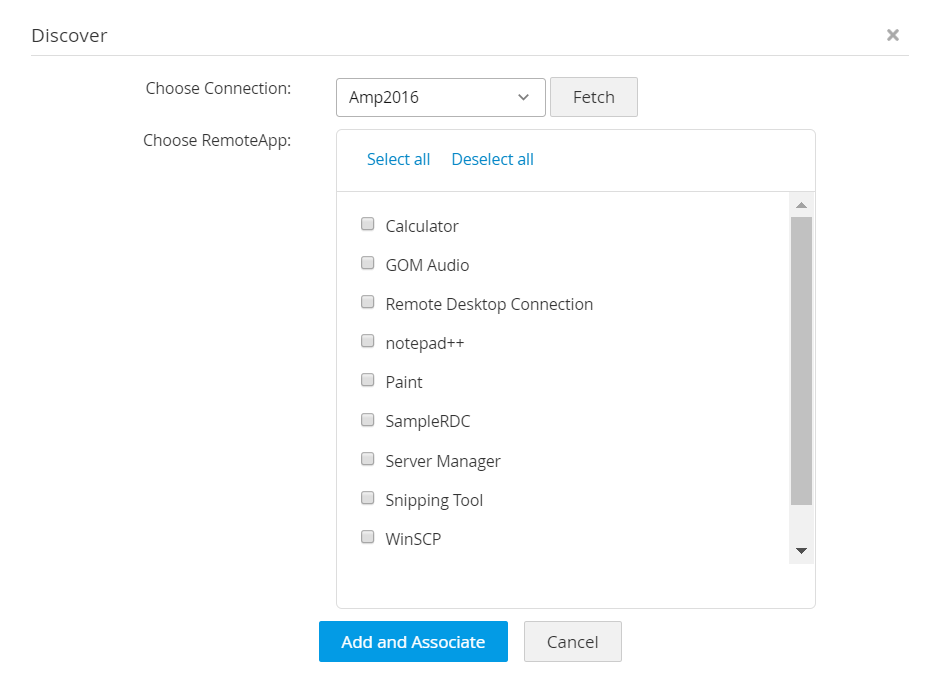
Discovering remote applications automatically: Access Manager Plus can discover remote applications from machines that already have them configured. IT admins can choose a remote resource and simply fetch all the required remote applications configured in that particular resource.
Once the chosen remote applications are added, the IT admins can associate them with any resource in Access Manager Plus.
9. Bi directional file transfer
What is a file transfer?
File transfer is the process of transferring files or data from one system to another over a network—locally, remotely, or via the cloud. Bundled with the right remote access management tool, file transfer enables admins to address security challenges, and track the movement of critical information within and across their enterprise network.
The need for secure file transfer tools
Today, most IT operations and integrations between software and applications require file transfer, and the volume and size of these files keeps growing. Users often need the ability to share large files with customers, third parties, and internal staff. However, because of the size limitations placed by IT administrators on the size of file attachments, users rely on third-party services for transferring large files. These file sharing services are insecure, and may even infect the files with malware or other security vulnerabilities. For organizations exchanging large volumes of data and requiring efficient file delivery, adopting traditional file transfer methods, like File Transfer Protocol (FTP) or email attachments, is simply ineffective and perilous.
When organizations operate on a global scale, transferring files from remote locations is often a daunting task. Sending files across the globe presents time constraints and challenges in managing the overall file transfer activities. Transfer of large files can be lengthy, resulting in connection losses and slow delivery.
Bidirectional file transfers via Access Manager Plus
Access Manager Plus provides a central console to streamline organizational file transfers, ensuring fast and simple transfers regardless of geographic location. It enables privileged users to transfer files between a remote system and the local host, or between two remote systems, based on their preset role permissions. It also enables admins to track mission-critical information flow within and across an enterprise.
Access Manager Plus supports bidirectional file transfer through the SSH File Transfer Protocol (SFTP). SFTP is an extension of FTP that adds support for data encryption, with no predefined size limit, allowing easy and secure transfer of even large files. It enables users to upload and download files up to 16MB per file between their host system and the remote resource through SFTP.
Access Manager Plus also provides access controls for file transfer activities. To perform file transfer on a resource for which access control is enabled, users need to send a password request to their administrator. Upon approval, users will be able to perform file transfers on that connection for the stipulated time.
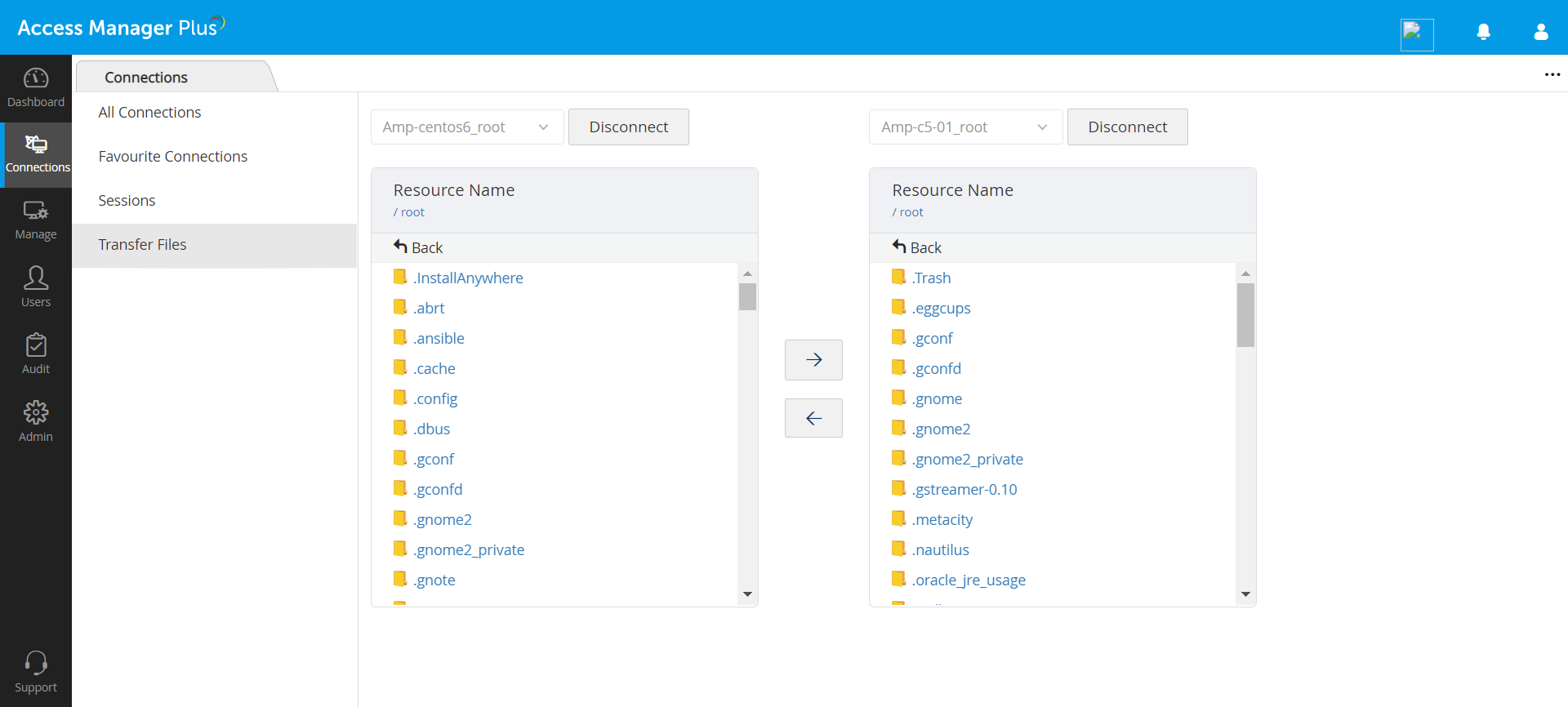
Seamless file upload and download capabilities
Apart from file transfer, Access Manager Plus allows users to upload and download files to and from any remote system without the need to initiate a remote session. Once Access Manager Plus authenticates the chosen resource, it will enumerate all the directories present in that particular remote system. Users can then choose the directory to or from which they need to upload or download files.
10. Privileged Session recording
What is a privileged session?
Privileged sessions are sessions initiated by privileged accounts with administrative access to critical systems and corporate data in the IT infrastructure.
Granting employees, system administrators, third-party vendors, or contractors uncontrolled access to critical systems poses potential security risks. Enterprises need to go beyond manual monitoring and traditional privileged session management workflows to gain proactive insights into all privileged activities, and minimize threats.
Privileged session management to fortify remote sessions
Privileged session management is a crucial IT security procedure that enables administrative users to gain granular control over critical assets, such as databases, servers, and network devices, providing greater accountability over privileged user accounts and systems.
ManageEngine Access Manager Plus offers cutting-edge features to monitor, record, and archive privileged sessions established through the web interface. Real-time session monitoring capabilities aid in detecting and terminating suspicious user sessions spontaneously to minimize any potential risk of a breach, helping security teams prevent any possible unauthorized use of classified accounts.
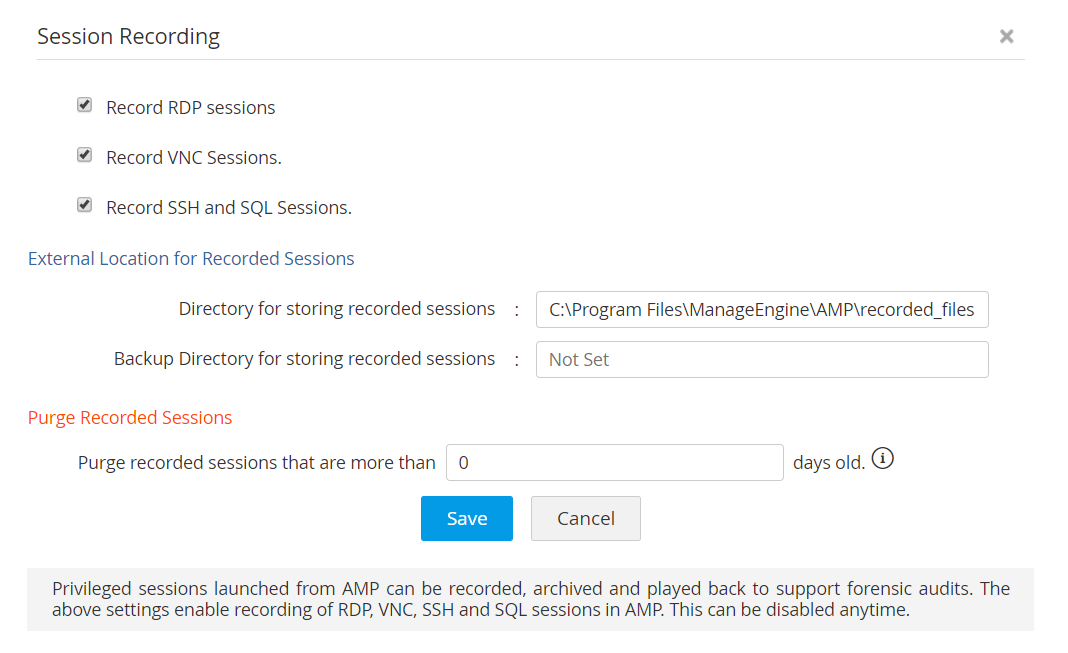
Enhanced privileged session recording and archival
By default, Access Manager Plus records all Remote Desktop Protocol (RDP), Virtual Network Computing (VNC), SSH, and SQL sessions launched from the application. You can also customize the external storage location to store the recorded sessions. The recorded sessions can be traced using any detail, such as the name of the connection, the user who launched the session, or the time at which the session was launched. If a privileged attack should occur, you can easily filter and review past session recordings to uncover the source, and adjust policies to prevent another attack. The recordings also aid in complying with regulatory standards like SOX, HIPAA, PCI DSS, and more.
Access Manager Plus includes a browser-based remote login mechanism for recording highly secure RDP, SSH, VNC, and SQL sessions without requiring third-party agents or plug-ins. Apart from session recordings, Access Manager Plus also offers archival of all activities.
Administrative users have the option to enable session recording by default for both specific and global sets of resources based on the session and session type. Recorded sessions can be archived in external directories, and users can set up additional storage locations for backup purposes.
Effortless management of privileged session recordings
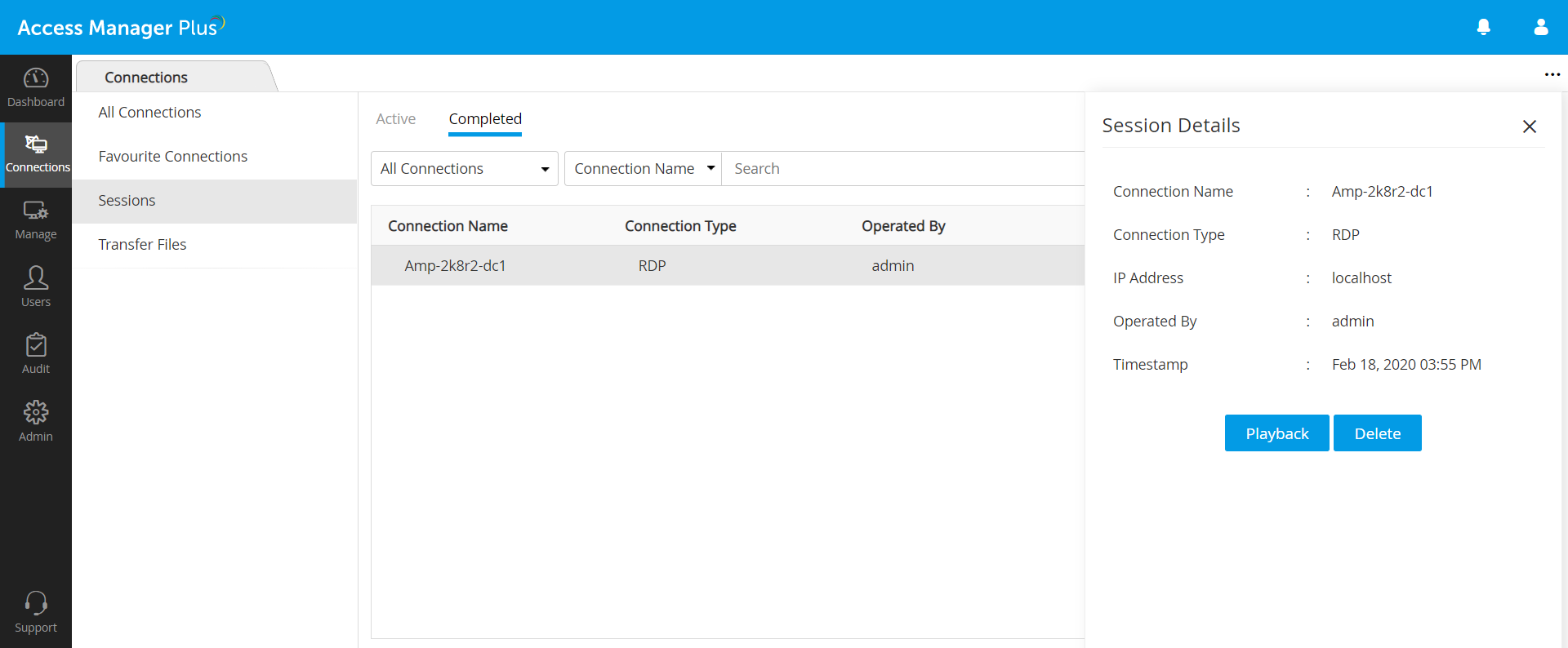
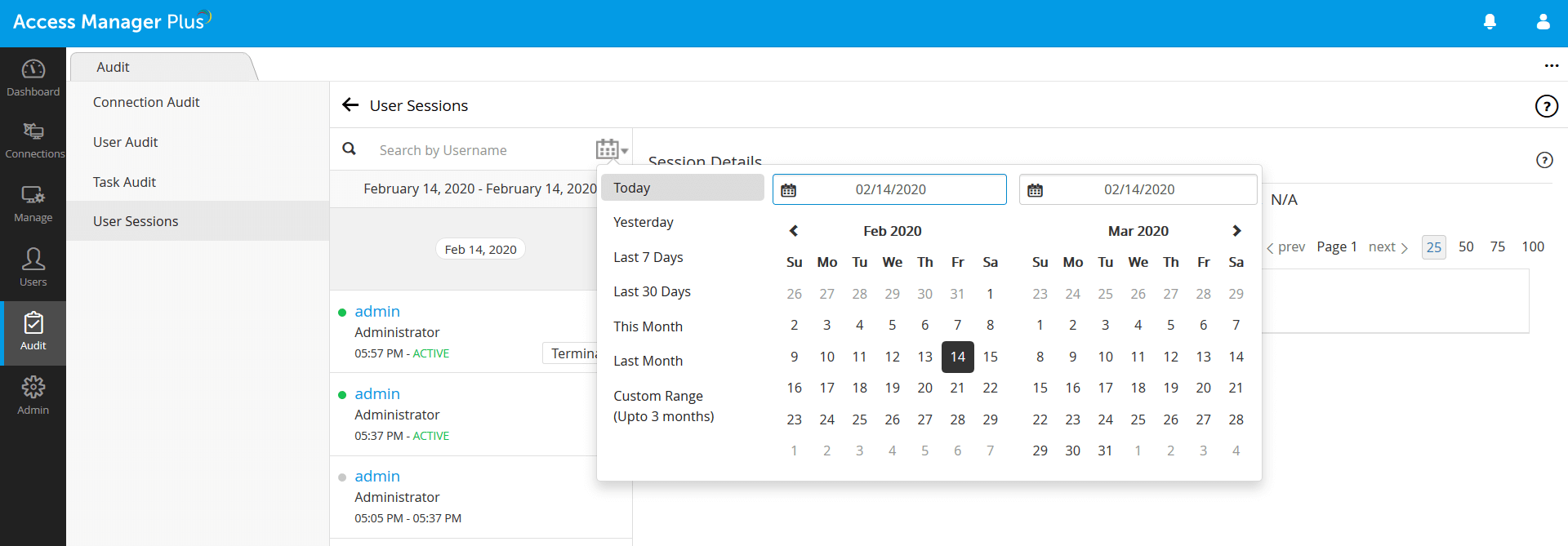
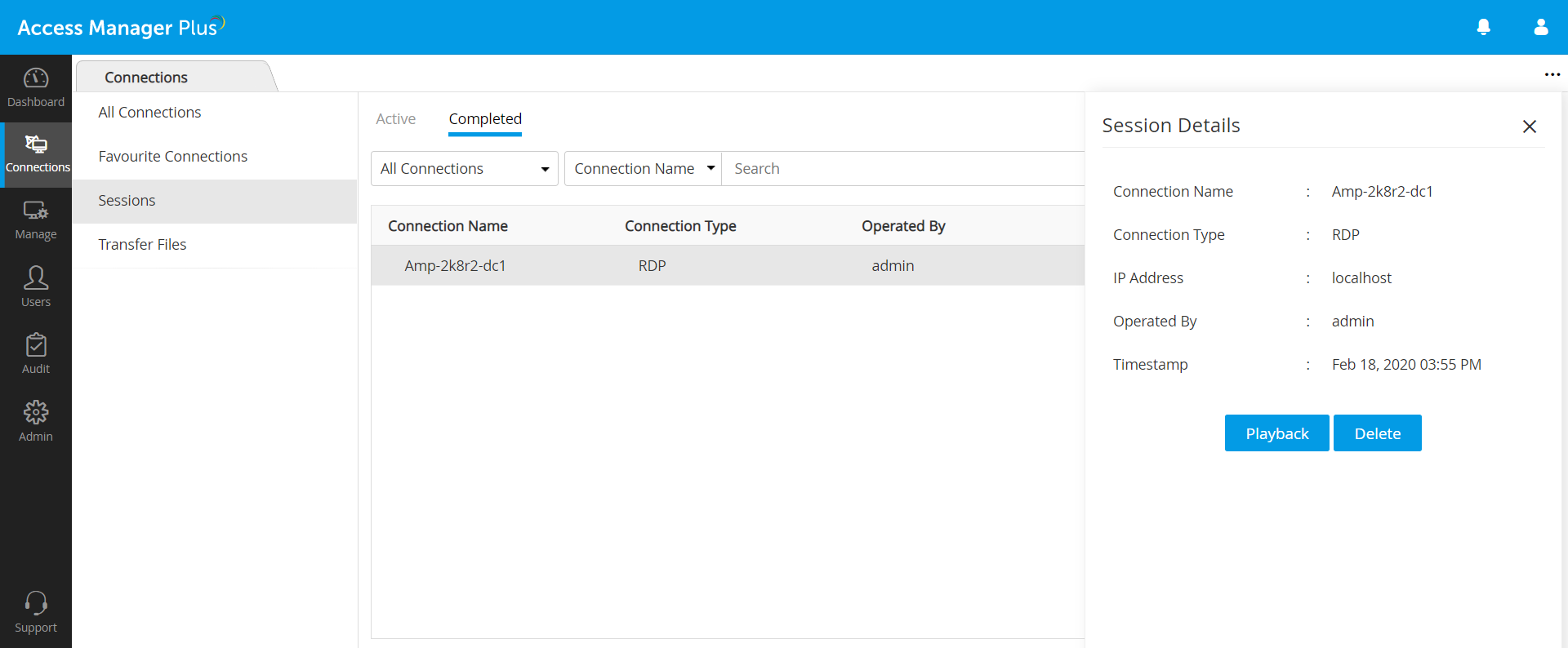
Session recordings and logs can be accessed almost instantly upon the completion of every remote session. The session details include the name of the connection, its type, IP address, timestamp, and the user who operated the session. Access Manager Plus provides a playback option to replay recorded sessions, which provides support for security and regulatory audits. Session recordings can be played either directly on the Access Manager Plus console, or by using the Remote Spark player with RDPV, SSHV, VNCV, or TELNTEV video formats.
Access Manager Plus provides the option to split large SSH or Telnet session recording files into smaller fragments to ensure smooth and uninterrupted playback. By default, files that exceed a size limit of 10MB are split into 10MB files for storage and encryption, and are compiled together into a single file during playback.
Regularly purge recorded sessions
If your organization is large and has a comprehensive range of resources for which session recording is enabled, the recorded sessions will naturally grow at a faster rate. You can purge recordings that are older than a specified number of days to keep disk space free, or store these recordings in the local drive so they can be moved elsewhere. You can delete a selective session or the chat history of a particular session. Users can also delete session recordings and logs from local storage as and when required.
11. Live monitoring and collaboration
What is a privileged session?
Privileged sessions are sessions initiated by privileged users or accounts with administrative access to critical systems in the IT infrastructure.
What is privileged session management?
Privileged session management is a crucial IT security strategy that enables admins to gain granular control over critical assets, such as databases, servers, and network devices. It enables security teams to monitor sessions and user activities in real time, identify and terminate anomalous sessions, and record all activities to support forensic audits and compliance standards such as HIPAA, SOX, and PCI DSS.
Access Manager Plus enables secure privileged sessions
Access Manager Plus provides a central web console to establish privileged sessions via Windows Remote Desktop Protocol (RDP), SQL, virtual network computing (VNC), HTTPS, and Secure Shell (SSH), and helps admins achieve high-level control and governance over user activities.
It offers cutting-edge features to monitor, record, and archive privileged sessions launched via the web interface. Real-time session monitoring capabilities help in detecting and terminating suspicious user sessions spontaneously to minimize any potential risk of a breach or access misuse.
Enhanced privileged session recording and archival
By default, Access Manager Plus records all RDP, VNC, SSH, and SQL sessions launched from the application. The recorded sessions can be traced using any details, such as the name of the connection, the user who launched the session, or the time at which the session was launched. If a privileged attack should occur, you can easily filter and review past session recordings to uncover the source and adjust policies to prevent another attack.
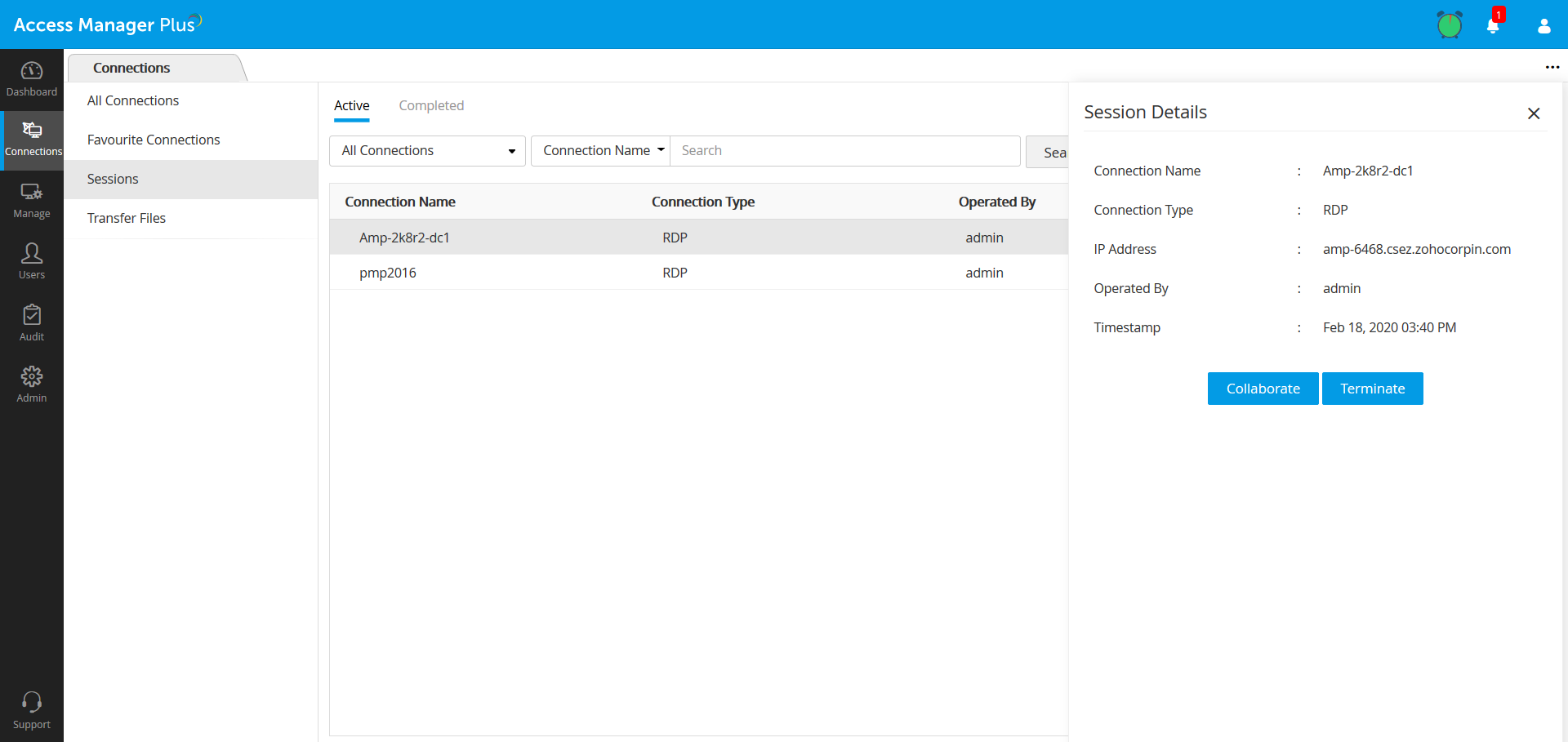
Real-time monitoring and shadowing of privileged sessions
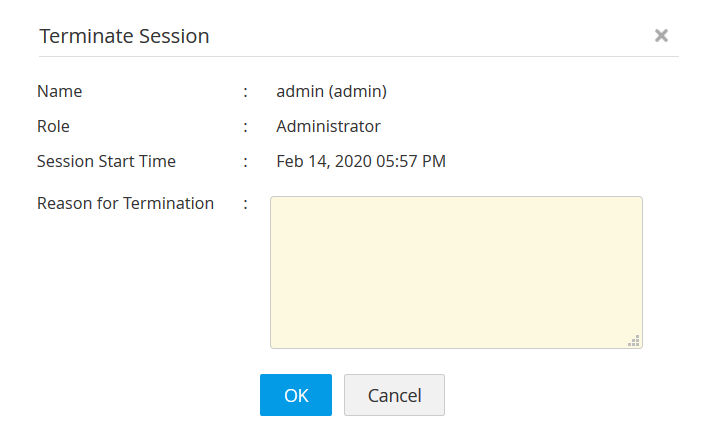
Access Manager Plus lets security teams monitor live and concurrent sessions initiated via RDP, SQL, SSH, and VNC connections. With exclusive session shadowing capabilities, it enables admins to join live sessions, monitor user activities, and terminate all suspicious and unauthorized sessions.
All privileged sessions are monitored as they happen. Admins can tune in to watch active privileged sessions that involve critical systems, possibly uncovering suspicious or unauthorized activities. The session termination option enables admins to terminate any suspicious or anomalous session instantly with the click of a button.
Additionally, admins can offer support to users when monitoring their activities during troubleshooting or collaborative sessions. Admins can also join active sessions and collaborate with other users simultaneously.
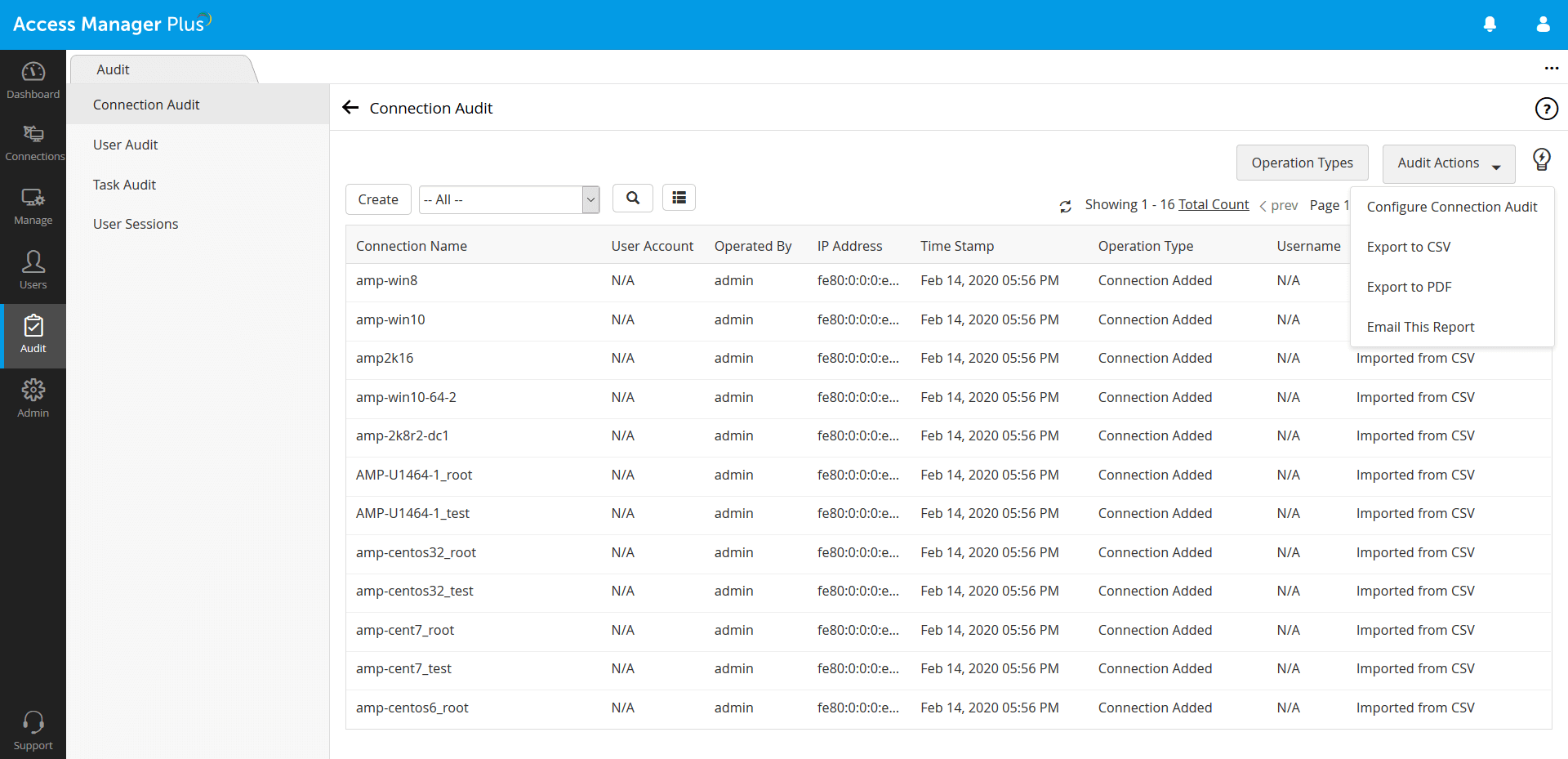
12. Audit Trails
What is an audit trail for privileged sessions?
An audit trail of a privileged session is a chronological record of events that provides basic information to trace all the activities performed during that session. Audit records of a privileged session may include what the event was, which user or application initiated the event (including IP address and device type), what operations were performed during the entire session, and the date and time of the event.
The need for comprehensive audit trails in IT security
Unmonitored access and its misuse is a serious problem for most systems. Capturing all the activities of privileged users is critical to identify and prevent anomalous actions that may harm business. Organizations must document the privileges granted to users, the actions performed with such privileges, and how these actions impact their IT environment. Traditional approaches to logging user activities cannot fully meet these requirements.
Audit trails help in identifying suspicious behavior. Through real-time monitoring and automated audit logs, administrators can identify system implementation issues, operational issues, unusual or suspicious activities, and other system errors.
Various compliance standards, like HIPAA, SOX, and PCI DSS, expect organizations to monitor and capture all actions performed by privileged accounts.
Facilitate regular internal audits and configure instant alert notifications
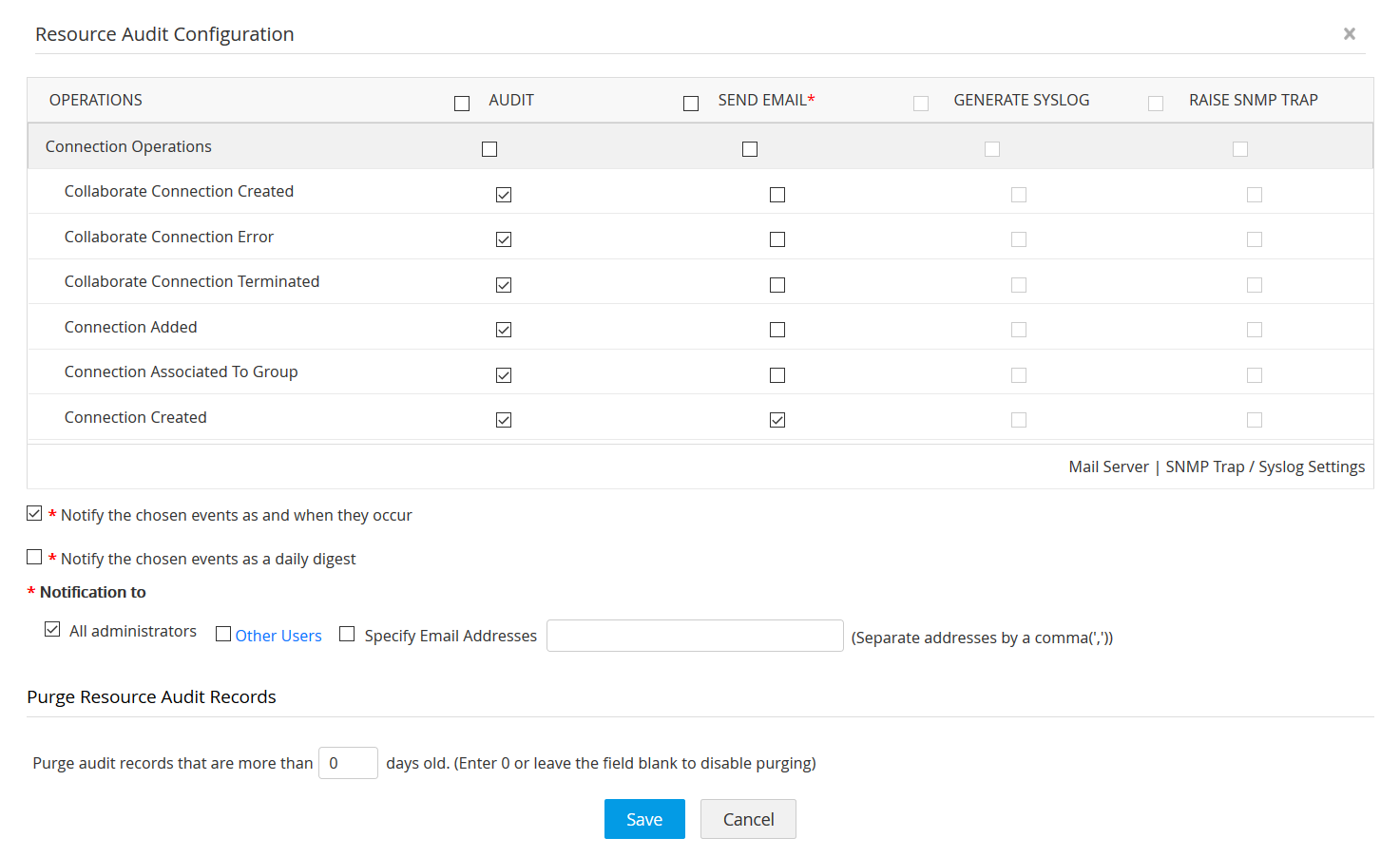
Access Manager Plus’ audit trails instantly record all events around privileged account activities, login attempts, and scheduled or completed tasks. This data helps in complying with regular internal audits and forensic investigations, demonstrating who accessed what resource or files, where, when, and why.
Only an administrator can view all the actions performed by other users. You can notify users of their activities through in-product notifications. Access Manager Plus also lets you send instant email notifications to specific recipients when certain events take place.
Demonstrate compliance easily with tamper-proof audit trails
Regulatory statutes such as HIPAA and SOX mandate proper maintenance of electronic records and require implementation of mechanisms for proper compliance and auditing. Access Manager Plus provides immutable audit logs that can be shared with auditors to demonstrate compliance.
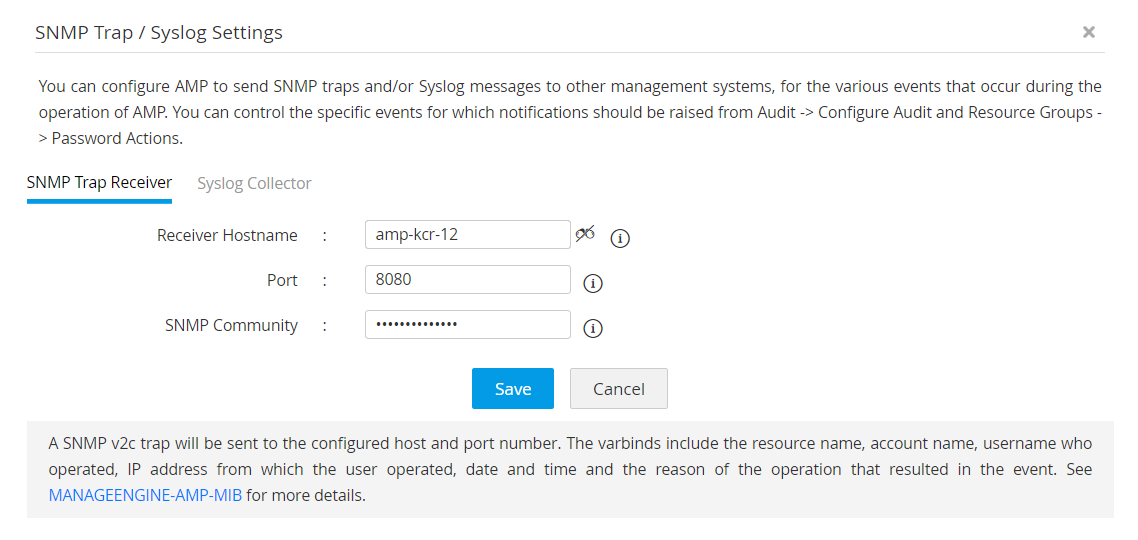
Send syslog messages and SNMP traps to your SIEM and network management systems
If you use a third-party security information and event management (SIEM) tool in your organization, you can integrate Access Manager Plus with the tool to send syslog messages for the various events that occur within Access Manager Plus. You can also integrate your network management tool with Access Manager Plus to receive SNMP traps.
These tools analyze and correlate privileged access data with other event data sourced from across the enterprise, helping security teams acquire a holistic view of privileged access and gain insights into suspicious activities.
Purge audit trails regularly to avoid storage clutter
If your organization is large, the captured audit logs will naturally grow at a faster rate. You can purge audit logs that are older than a specified number of days to keep the disk space free. You can also store these logs in the local drive, and move or delete them as required.