Product Overview
What is Delinea Server PAM
Server PAM controls privileged access to servers in both on-premise and cloud/multi-cloud environments and allows humans and machines to seamlessly authenticate with passwordless login, enforcing least privilege with just-in-time privilege elevation, preventing lateral movement, increasing accountability, and reducing administrative access risk.
Server PAM simplifies user authentication and passwordless login to servers by consolidating identities across Active Directory and the most popular cloud directory services while enforcing multi-factor authentication (MFA) for stronger identity assurance.
Specifications
Protect your servers from cyber risk, centralize management and easily meet compliance requirements
Enhance Security & Mitigate Risk
Enforce just-in-time (JIT) and just-enough (JE) privileged access with multi-factor authentication (MFA) enforcement at system login and at privilege elevation to prevent lateral movement and align with least privilege and Zero Trust best practices.
Consolidate Identities & Improve Productivity
Eliminate the large number of unmanaged local accounts to greatly reduce the attack surface and use enterprise directory accounts to access Windows, Linux or Unix on-premise or in the cloud.
Meet Compliance Mandates & Incident Investigation
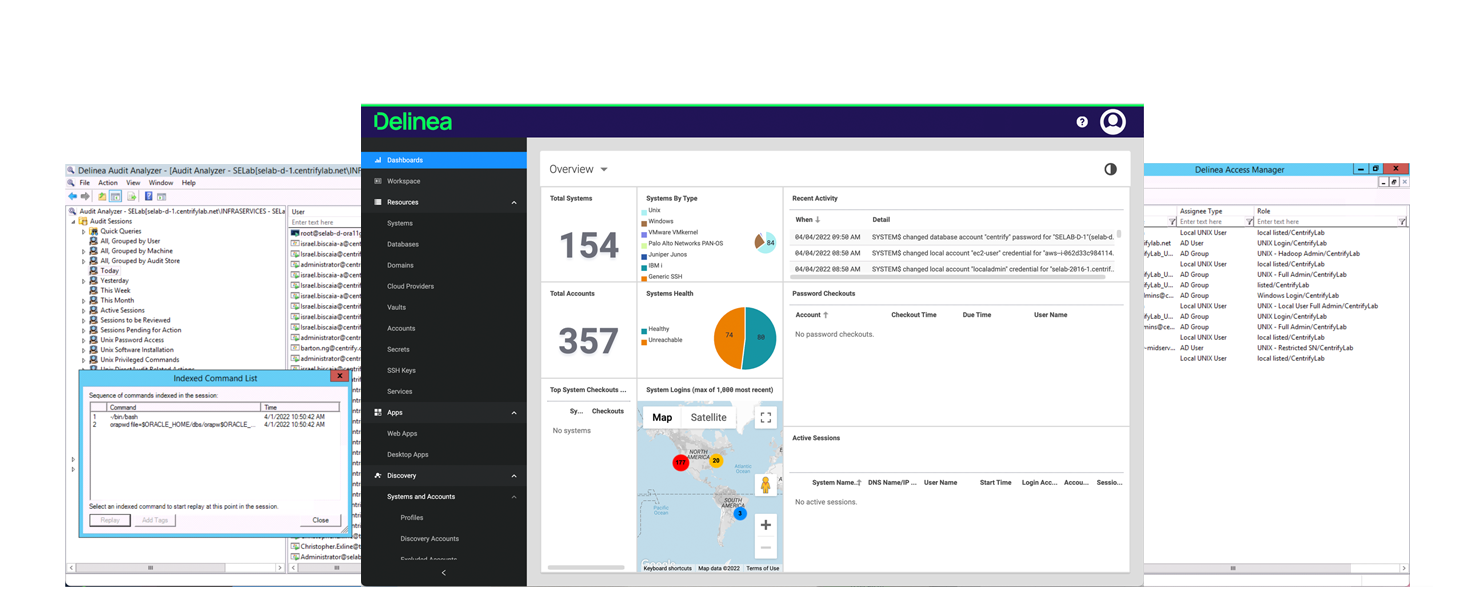
Leverage granular, host-based auditing and session recordings to prove compliance and to aid in the investigation of incidents across on-premise and cloud servers.
Secure and consolidated identity access to improve productivity; manage privileges and protect against cybersecurity
Delinea’s Server PAM solution controls privileged access to servers in both on-premise and cloud/multi-cloud environments and allows humans and machines to seamlessly authenticate with passwordless login, enforcing least privilege with just-in-time privilege elevation, preventing lateral movement, increasing accountability, and reducing administrative access risk.
Centrally manage login, execution, and MFA policies in Active Directory (AD) (patented zones) or from cloud identity providers. Single enterprise identity for user login.
Minimize risk with best practices
Align with regulations and best practices such as Zero Trust and zero standing privileges to protect against ransomware and data breach attacks.
Enforce least privilege
Role-based access control (RBAC) at the host level for fine-grained control and privilege elevation. Self-service workflows for just-in-time access requests.
Enforce adaptive MFA
MFA policies enforced at login and application execution across Windows and Linux for stronger identity assurance and cyber risk insurance demands.
Improve security and compliance
Forensic level audit trails and session recordings for security review, incident response, compliance, and full accountability.
Modern, scalable architecture simplifies the management of privileged access to complex server environments
- Centralized identity and policy management across various identity providers
- Choice of cloud identity providers or Active Directory through patented Zone technology
- Multi-directory brokering
- Multi-Factor Authentication (MFA) enforcement everywhere
- Granular host-based auditing and session recording
- Identity consolidation to reduce attack surface
- Consistent enforcement of least privilege for Zero Trust