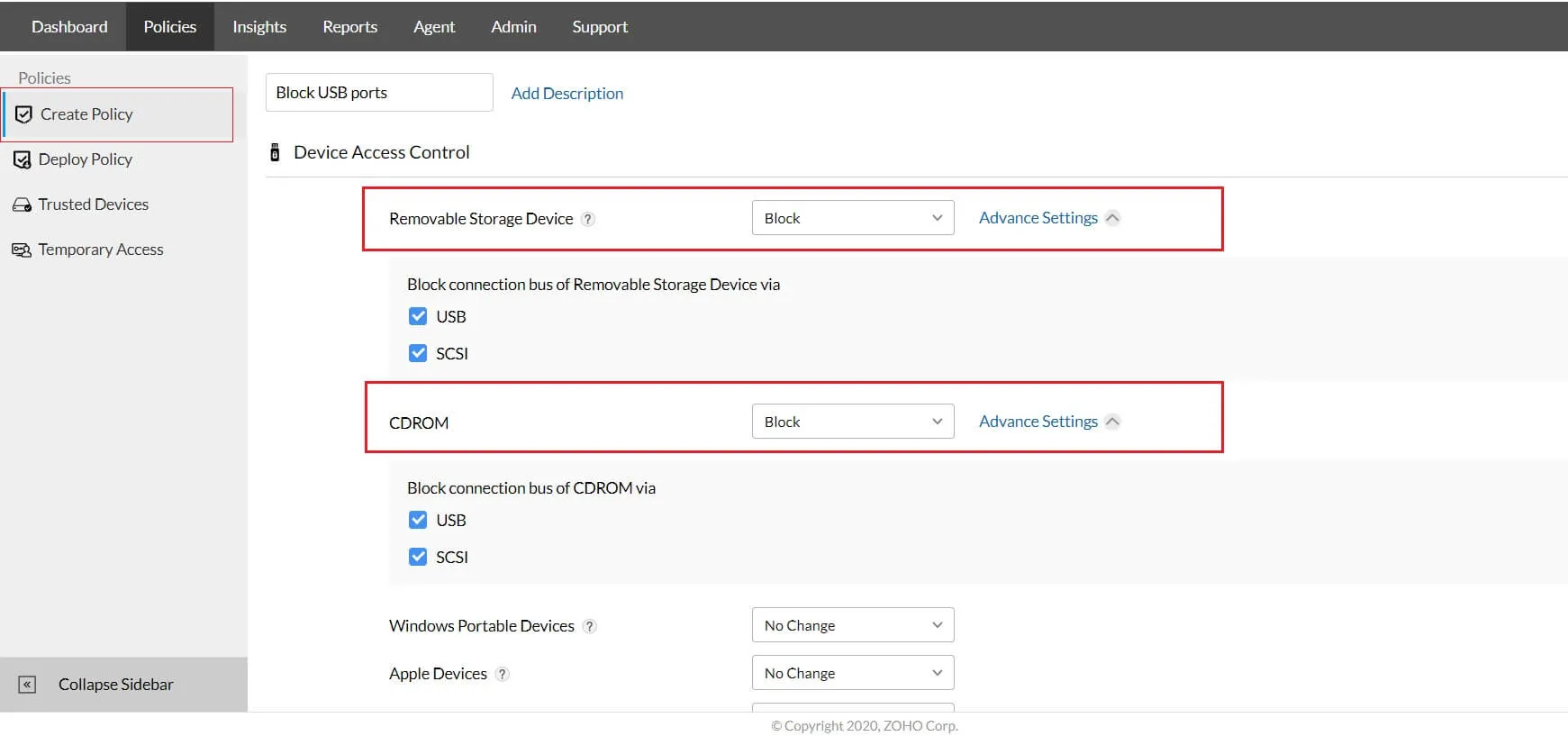
Product Overview
Device Control Plus is an enterprise solution from ManageEngine that monitors and controls the different peripheral devices that connect to endpoints across a business IT network. It can extend control over a variety of external devices such as USB devices, CDROMs, printers, modems, network adapters and more.
Device Control Plus is purpose-built to prevent data leakage through removable devices and eliminates the intrusion of malware from unsafe devices, thereby contributing to improve overall security. The product locks all ports across systems, providing IT administrators complete control over the accessibility of external device.
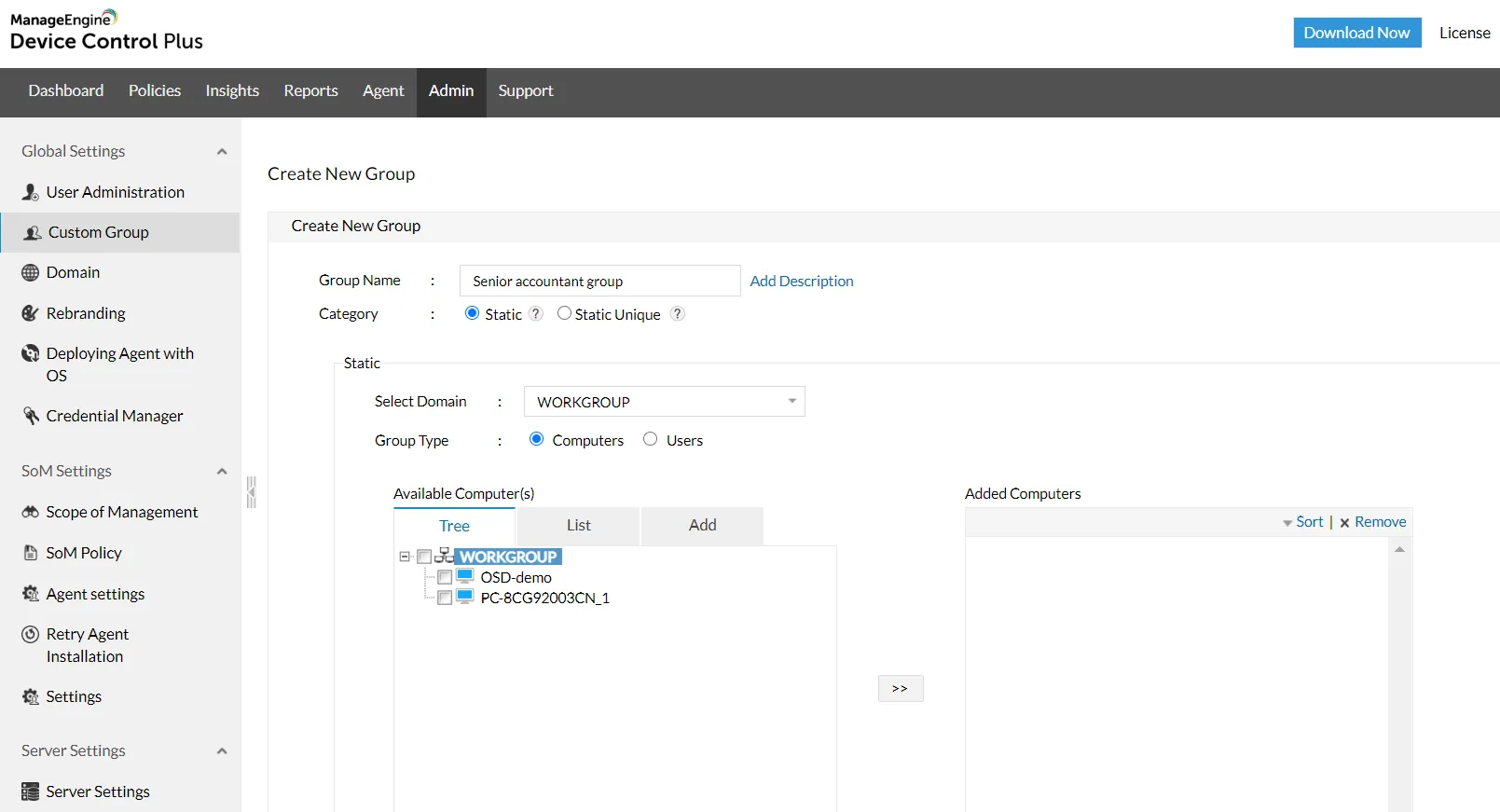
IT admins can use the trusted device list to monitor external devices in real-time and receive notifications when end-users plugs in unauthorized devices. Device Control Plus also enables users to grant access permissions based on the role of users within the enterprise. Additionally, admins can grant temporary access to users for a specified period of time.
Specifications
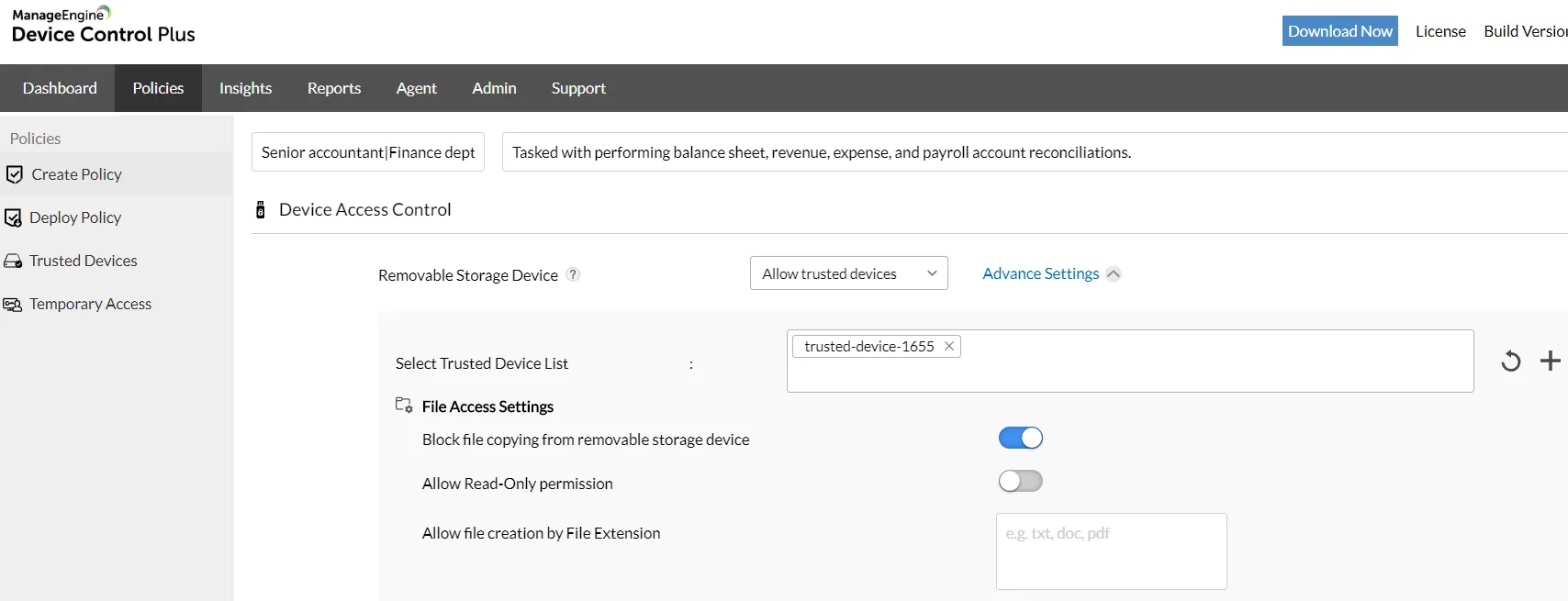
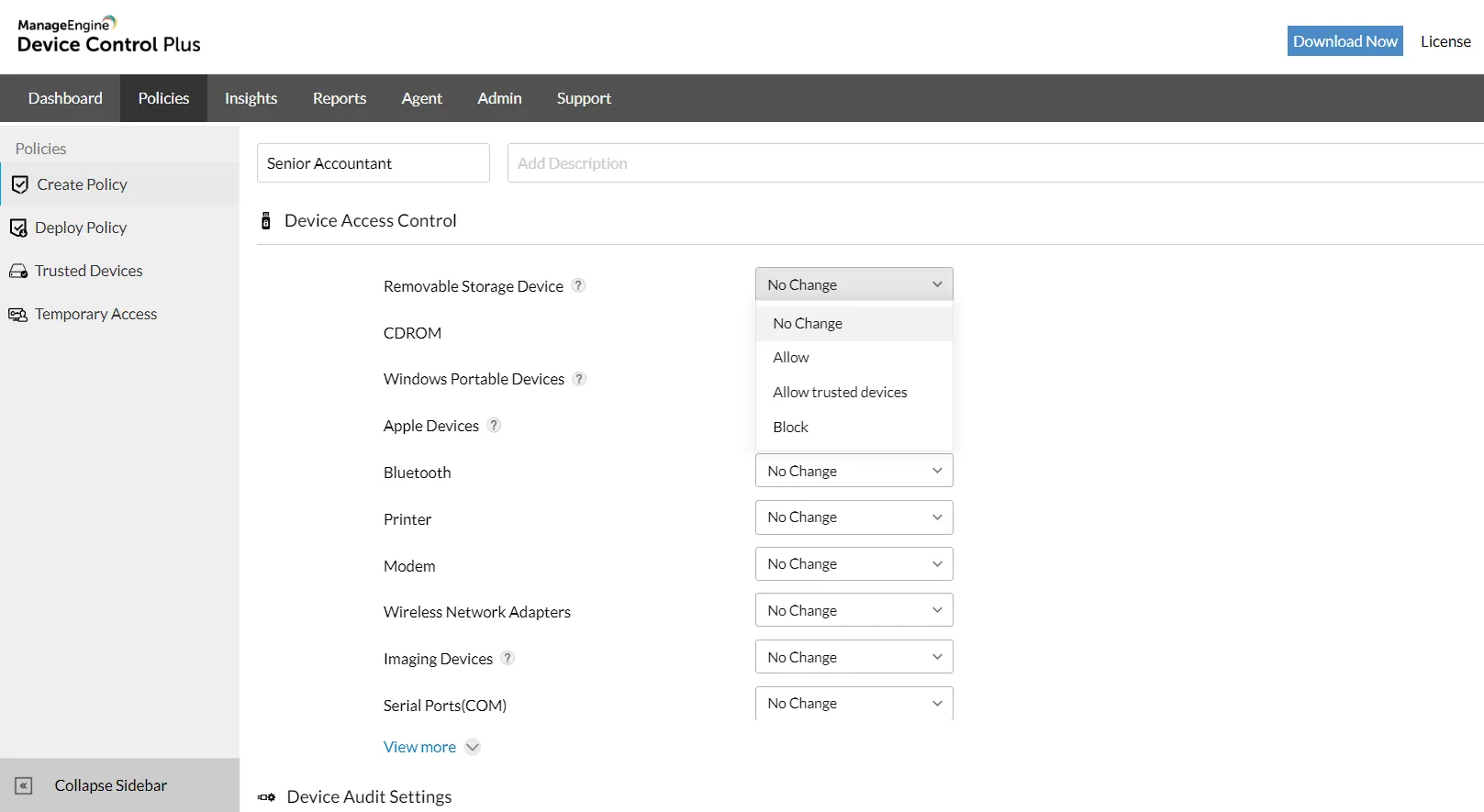
Device & port control
Control all ports and connected removable devices, block unauthorized access to your data and monitor all device & file actions effectively.
File access control
Prevent data loss with strict role based access control policies - set read only permission, block copying of data from devices and do more.
File Transfer Control
Curb unprecedented data transfers - limit file transfers by setting the maximum file size and type of file that can be transferred from your computer.
Trusted Device List
Create exclusive access for devices to access your computer by adding them to the trusted device list.
Temporary access
Create secure and temporary access for devices to access your computers when they want to access what they want to access
Reports and Audits
Maintain records of devices, users and computers that are managed. View all device actions and data usage activities.
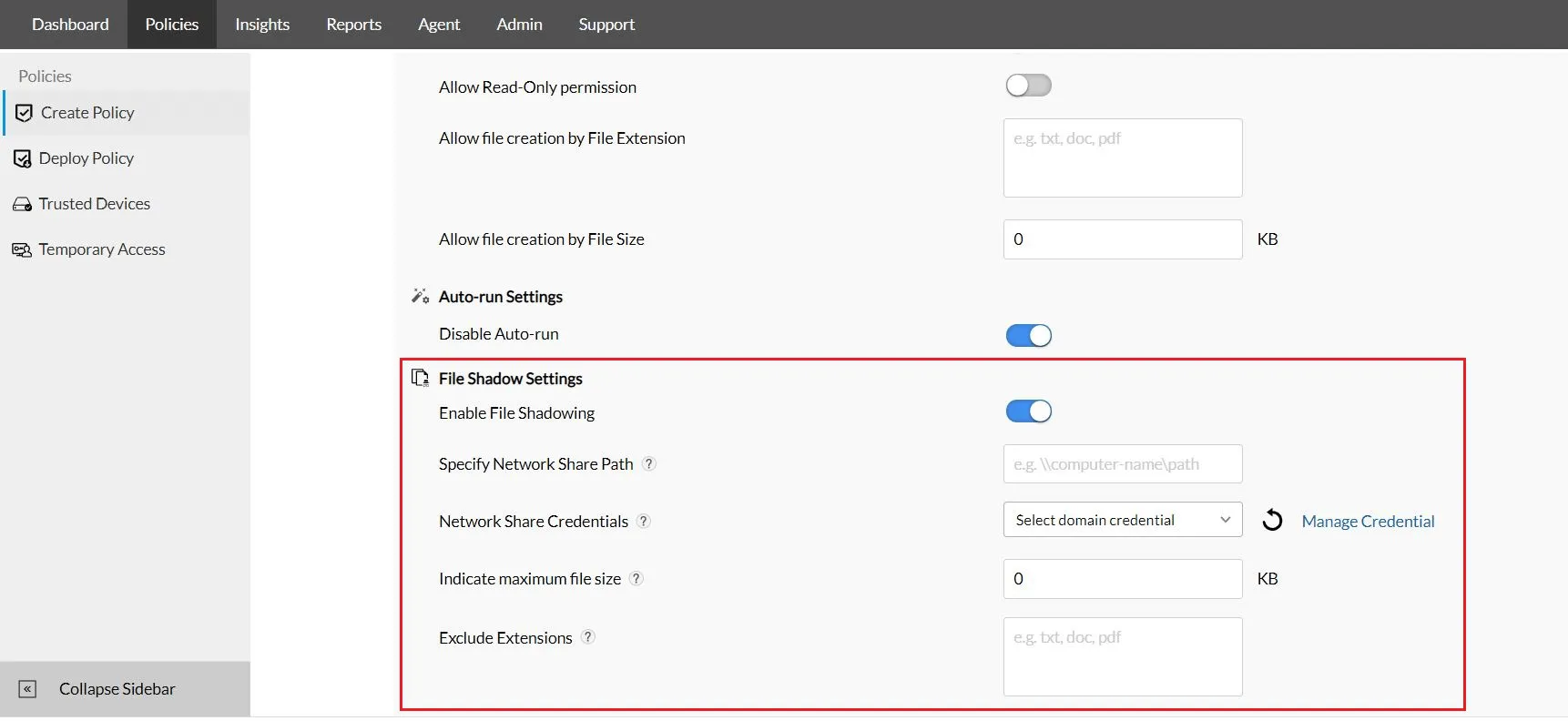
File Shadowing
Effectively secure files involved in data transfer operations by creating and storing mirror copies in password-protected shares.
File Tracing
Monitor file actions in real time, record salient details such as file names and locations along with the computers, devices and users involved.