Product Overview
- Get log data from systems, devices, and applications
- Search any log data and extract new fields to extend search
- Get IT audit reports generated to assess the network security and comply with regulatory acts
- Get notified in real-time for event alerts and provide quick remediation
You can use EventLog Analyzer to:
- -Monitor network activities of servers, workstations, devices, and applications spread across geographies
- -Monitor user activities like user logons/logoffs, failed logons, objects accessed, etc…
- -Generate reports for top network events, user activities, and network event trends
- -Generate compliance reports for PCI-DSS, HIPAA, FISMA, SOX, GLBA and other regulatory acts
- -Perform log forensics by searching across any log format and save the search results as reports
- -Configure automatic alert notification through email or SMS for specific events, network anomalies and compliance threshold violations
- -Execute custom scripts or programs on alert generation to automatically remediate the security issue
- -Create custom IT reports to address internal security audit
- -Create custom compliance reports for IT Auditors
- -Schedule reports for auto generation and distribution
- -Tamper-proof and secure archival of log data for forensic analysis and compliance audits
Specifications
-Log management
- Collect and analyze logs from all your end-user devices on a single console.
- Syslog management
- Collect and analyze syslogs from various devices and gain insights on network activities that are displayed through intuitive graphs and reports.
- Universal log collection
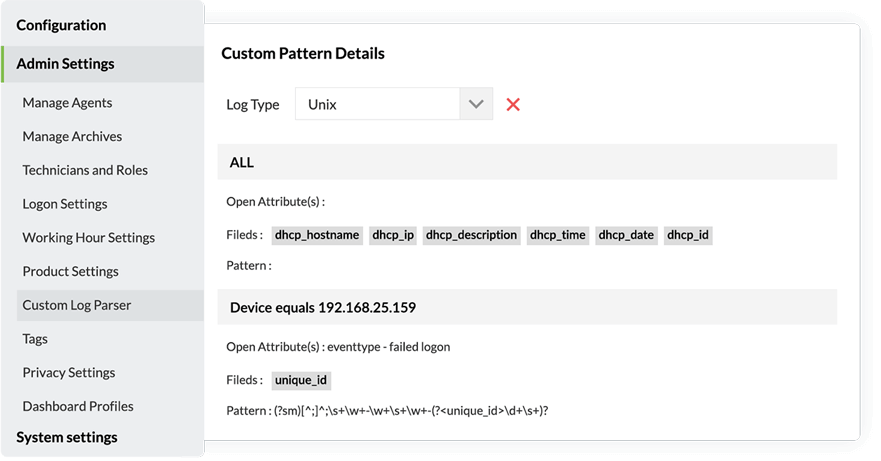
- Collect logs from multiple log sources such as Windows and Unix and Linux systems, IBM AS/400, applications, databases, firewalls, routers, switches, IDS/IPS, and your Cloud infrastructure.
- Application log management
- Manage application logs and gain in-depth security information on incidents through predefined reports and real-time alerts.
- Event log management
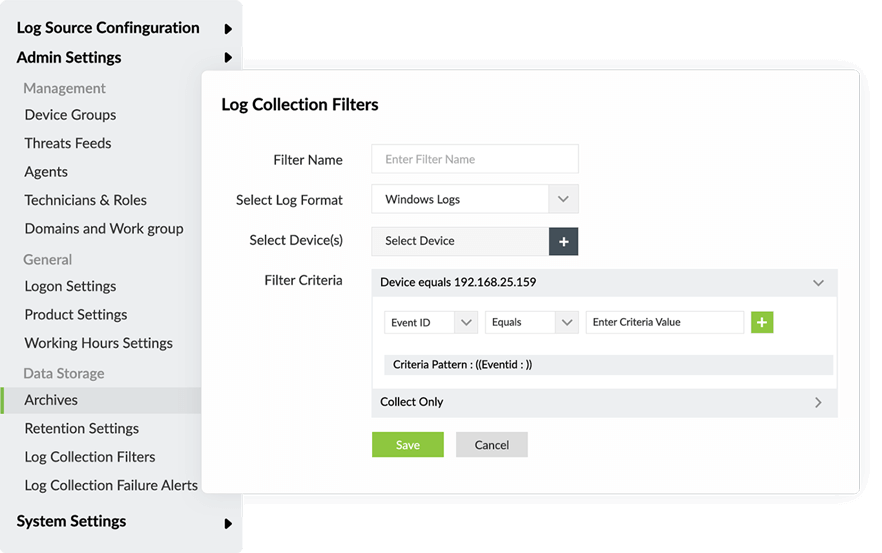
- Collect, filter, parse, analyze, correlate, search, and archive event logs.
- Agent based log collection
- Collect event logs from your devices with agents.
- Agentless log collection
- Collect event logs from your devices without the need for a separate agent.
-Application auditing
Audit all your critical application servers and monitor custom applications.
- Application log monitoring
- Monitor monitor web server applications such as IIS and Apache, databases including Microsoft SQL Server and Oracle, DHCP applications.
- Microsoft SQL Server auditing
- Monitor all database activities, accesses, and server account changes in your Microsoft SQL Server database.
- Microsoft SQL Server monitoring
- Monitor server activity such as server startups and shutdowns, backup and recovery, SQL trace activity, and more.
- Microsoft IIS web server log analyzer
- Monitor IIS web server logs and receive alerts on server usage, errors, and any attack attempts.
- Microsoft IIS FTP server log analyzer
- Collect and track IIS FTP logs and gain intuitive and actionable insights on user activity, FTP file operations, and more.
- Microsoft IIS server auditing
- Audit, manage, and track IIS web servers.
-Network Device Auditing
Monitor all your important network devices such as your firewalls, routers, and switches.
- VPN log monitoring
- Gain actionable insights on VPN user details, audit VPN logins, and analyze trends in login patterns.
- Router and switch log auditing
- Monitor router traffic and user activity in your HP and Juniper devices, and identify suspicious events that threaten your network security.
- IDS/IPS log monitoring
- Collect IDS/IPS logs and access them from a centralized location. Obtain valuable network threat information about attack types, targeted devices and more.
-IT compliance management
Meet regulatory requirements with ease.
- Complete resource auditing
- Easily meet compliance regulations such as PCI DSS, SOX, HIPAA, ISO 27001, GDPR, FISMA, GPG, GLBA, ISLP, and Cyber Essentials.
- Customized compliance reports
- Create custom compliance reports that suit your requirements.
- Reports for new compliance
- Create custom reports for new compliance mandates.
-Security analytics
Detect security events and gain actionable insights on them with an advanced security analytics mechanism.
- Syslog monitoring
- Enhance network visibility and security on a centralized syslog server.
- Event log monitoring
- Collect and monitor event logs from your Windows devices and gain in-depth reports and real-time alerts on suspicious activities.
- Search
- Stay on top of security events of interest by saving search queries as alert profiles so you get alerted to suspicious activity instantly.
-Threat analytics
Secure your network and safeguard it against unwanted breach attempts and critical data theft through threat detection and mitigation.
- Windows threat detection
- Protect your security tools such as vulnerability scanners, endpoint security protection tools, and perimeter security devices.
- File integrity monitoring
- Track critical changes such as creation, deletion, access, modification, and renames on your files and folders, and get alerted to suspicious activity.
- Linux file integrity monitoring
- Detect changes made to files, folders, and directories in Linux systems.
- Privileged user activity auditing
- Track privileged user activity and detect suspicious events such as unauthorized logons, logon failures, and access attempts during non-working hours.
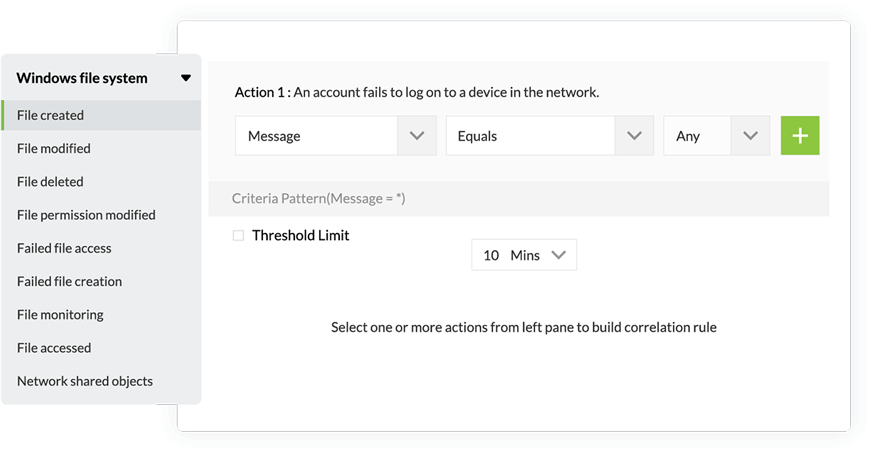
- Real-time event log correlation
- Detect security threats accurately and identify attack patterns by correlating suspicious events across your network.
- Threat intelligence
- Get alerted to malicious traffic to or from blacklisted IP addresses, domains, and URLs in real time through the built-in STIX/TAXII feed processor.
-Cross-platform Audit
Meet auditing needs by utilizing prebuilt reports for all your network devices including Windows, Unix and Linux, IBM AS/400, cloud platforms, vulnerability management systems, and your critical files and folders.
- Critical server monitoring
- Monitor server activities in real time to track errors and detect security threats.
- Event log auditing
- Collect, parse, and audit Windows event logs in your network. Utilize predefined reports and alerts to stay on top of suspicious activities.
- VMWare server log management
- Simplify virtual infrastructure log monitoring by centrally collecting, analyzing, and archiving virtual machine logs.
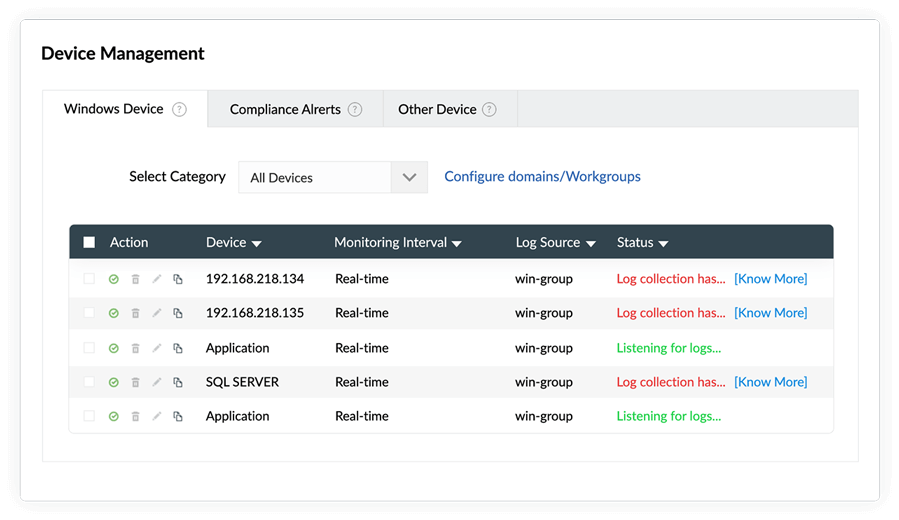
- Windows device auditing
- Gain an overview of all network activities on your Windows devices. View important events based on the severity level, device, and trends.
- Syslog device auditing
- Gain an overview of all network activities on your syslog devices. Track events based on the severity level, device, and trends.
- IBM AS/400 reports
- Manage IBM AS/400 logs, conduct forensic analysis, meet compliance requirements, and ensure file integrity.